Questo articolo è disponibile anche in lingua italiana, al seguente link – Active Directory: configurare il Cloud Kerberos – WindowServer.it
Going back to 2015, when Windows 10 was released, one of the biggest innovations revolved around Windows Hello for Business. It wasn’t so much the novelty itself, as it was inherited from Windows 8, but rather its integration with various Single Sign-On systems, software, and security prospects.
Over time, the integration of Windows Hello for Business has become increasingly easier, although it must be said that this tool was not immediately “convenient” to implement for those with a hybrid infrastructure, predominantly on-premises. The requirement to use a digital certificate, and therefore an internal CA, was not exactly for everyone; unlike full cloud scenarios, where the deployment of Windows Hello for Business happens in a few minutes, the steps were many and lengthy.
“Simplicity” arrived a few years ago, when a new integration option called Cloud Kerberos was released; this allows the use of Microsoft Entra to perform key exchanges even for on-premises objects, benefiting from the functionalities of Windows Hello for Business without using digital certificates or other complex tools.
PIN Dilemma
When it comes to the PIN, many IT Admins contest the low security of a numeric validation system, which could be easily found. This condition is true, but only partially: the complexity of the PIN can be defined, but more importantly, the PIN always remains a step after the password, which as a concept does not disappear from Active Directory, nor from Microsoft Entra ID. Therefore, I can have an ultra-complex password that ends up being forgotten, while the PIN can be entrusted to the user, with a complexity and rotation policy that does not affect the primary identity of my users.
Another aspect not to be forgotten is that Windows Hello for Business also legitimizes the use of more advanced tools, such as biometrics or FIDO2 keys.
Kerberos Server Configuration
Before starting, make sure that your infrastructure, at the Domain Controller level, has machines with at least Windows Server 2016 – much better 2022 or 2025. In multi-domain environments, this operation will need to be performed in each domain of the forest.
Within one of the Domain Controllers, execute the following PowerShell commands:
[Net.ServicePointManager]::SecurityProtocol = [Net.ServicePointManager]::SecurityProtocol -bor [Net.SecurityProtocolType]::Tls12
Install-Module -Name AzureADHybridAuthenticationManagement -AllowClobber
The next step will be to create an object in Active Directory, necessary for the integration of Cloud Kerberos. By default, the cmdlet Set-AzureADKerberosServer uses commercial cloud endpoints. To get a list of available clouds and the necessary numeric value for modification, and to install some necessary components, execute the following command: Get-AzureADKerberosServerEndpoint.
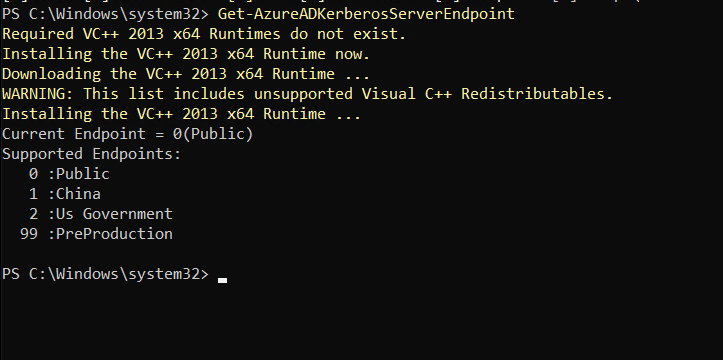
To create the component in AD, there are four credential insertion modes, which you can find at the following link – https://learn.microsoft.com/en-us/entra/identity/authentication/howto-authentication-passwordless-security-key-on-premises#example-1-prompt-for-all-credentials – for this demo, we will use option 4. Execute the following commands:
$domain = $env:USERDNSDOMAIN
$userPrincipalName = “administrator@contoso.onmicrosoft.com”
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName
To verify that the operation was successful, run the following command: Get-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential (get-credential)
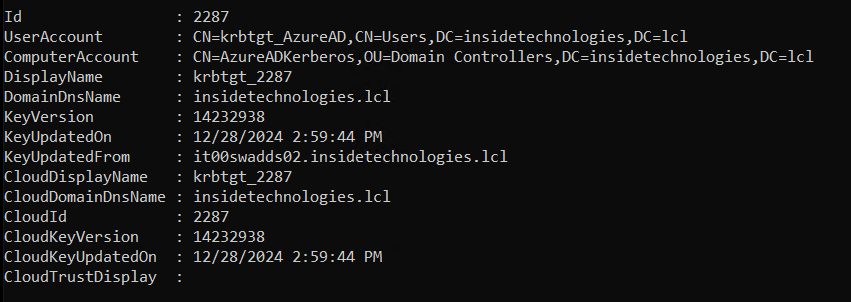
Within the OU Domain Controllers, a new object called AzureADKerberos will appear.
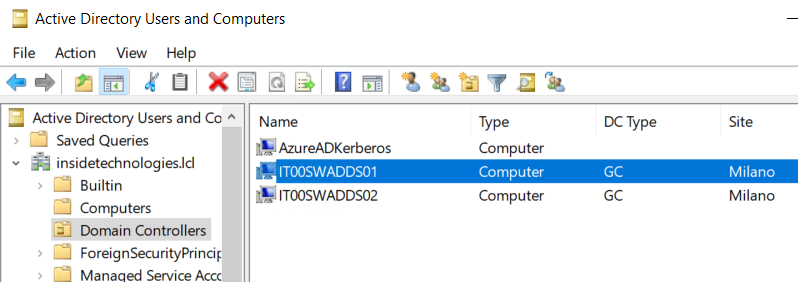
Policy Creation
Cloud Kerberos configuration, from client side, goes through Microsoft Intune or GPO. I have often explained how the use of cloud policies, even for scenarios with Domain Controllers, helps IT Admins manage their devices more securely, allowing them to distribute policies on the fly that can be received by any device (even without being connected to the network via VPN).
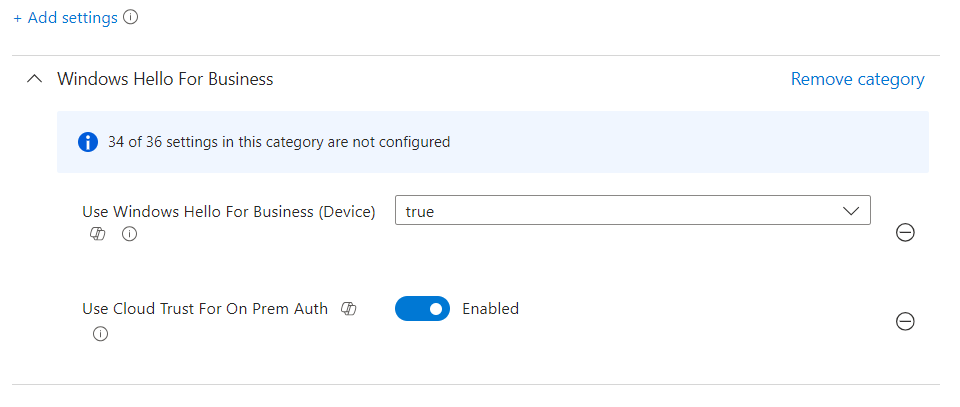
Within Microsoft Intune, create a new Settings Catalog policy setting the presence of support for “Use Cloud Trust For On Prem Auth”.
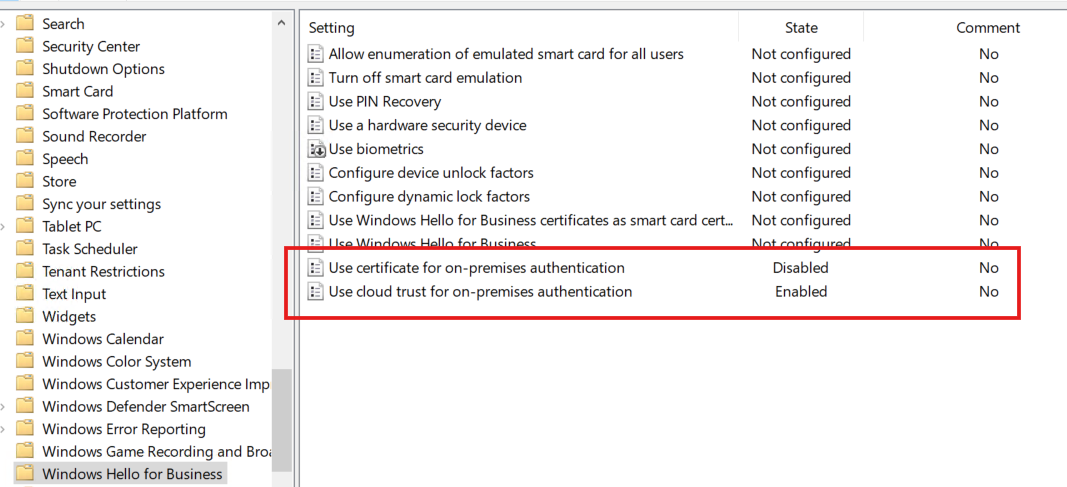
For those who want to use traditional GPOs, it is necessary to activate the following policy.
Client PIN Setup
To use Cloud Kerberos, the client must be at least Windows 10 22H2. In truth, it has been possible to use it since build 2004, but since it is widely out of support, we consider the latest still good build of Windows 10.
To avoid any problems, it is good to clean up all the various objects and reconfigure the PIN from scratch. To do this, follow these steps on the client you want to test:
- Start cmd (or Terminal)
- Execute the command certutil -deleteHelloContainer
- Restart the PC and log in with the password
- Configure the PIN
- Disconnect the user session and log in with the PIN
The suggestion is to wait for the deployment of policies and the various syncs of Entra Connect, which obviously must already be configured to host the hybrid mode of the objects.
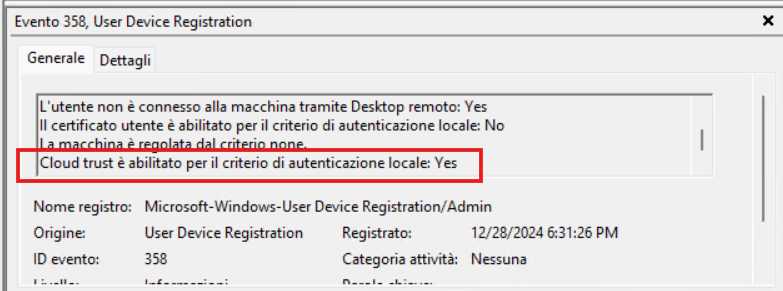
To verify that the client has started using Cloud Kerberos, you can check the Windows event viewer, within the Microsoft – Windows – User Device Registration – Event 358 section.
Another place to correctly check the functionality is in Active Directory and specifically in the attributes of the PC used for the test; a value should appear in the msDS-KeyCredentialLink key.
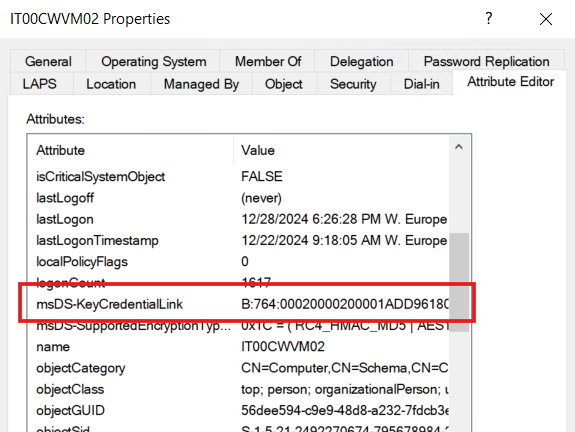
And voilà, from now on your users will be able to forget their passwords.
Rotation of the Entra Cloud Kerberos Server Key
The Microsoft Entra Kerberos server encryption krbtgt keys should be rotated on a regular basis. Iyt is a good practice that you follow the same schedule you use to rotate all other Active Directory DC krbtgt keys. To do this, it is necessary to execute the command: Set-AzureADKerberosServer -Domain $domain -CloudCredential $cloudCred -DomainCredential $domainCred -RotateServerKey
Conclusions
The use of Cloud Kerberos legitimizes the use of Windows Hello for Business within any company that is still “tied” to an on-premises infrastructure. The suggestion is to implement the use of the PIN from today, which will make access easier and guarantee IT Admins a stronger modification of the various users’ passwords.
#DBS