Questo articolo è disponibile anche in lingua italiana, al seguente link – Azure Arc & Log Analytics: raccogliere gli event log custom – WindowServer.it
In recent months, we have published several articles explaining how Azure Arc can fetch information from our servers and then transfer it to Log Analytics. In this article – How to enable File Server logs with Azure Arc & Log Analytics – we have seen, for example, how to retrieve logs from a file server using both the classic Event Viewer and Microsoft Defender for Endpoint. But how does the event retrieval process work when we want to be “targeted” within the Windows Server event viewer? That is what we will see in this article.
Configuration
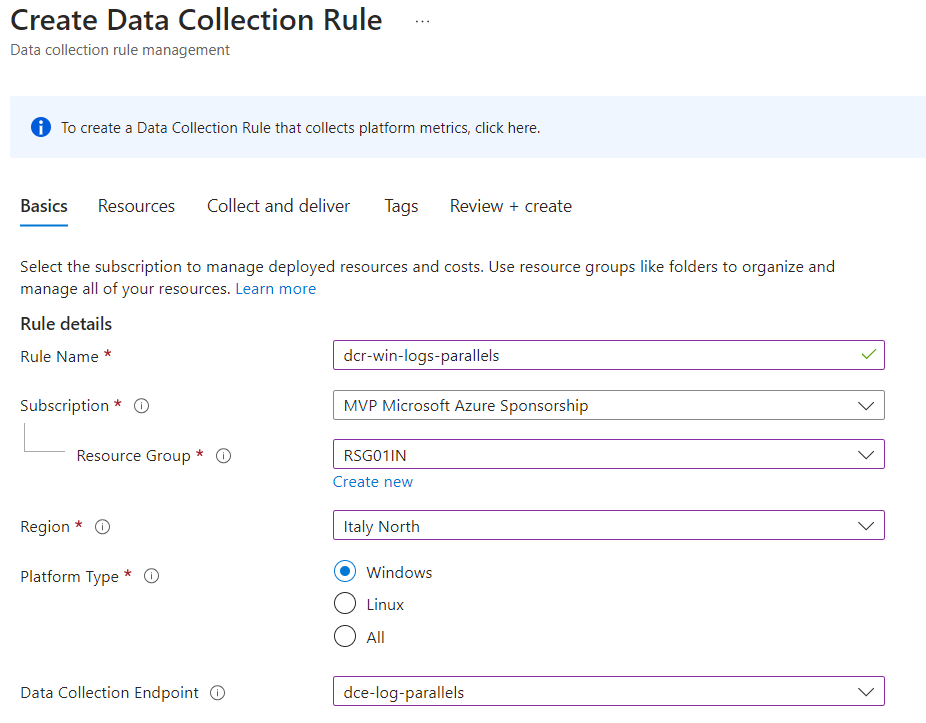
First, the procedure is always the same: first, install the Azure Arc agent on the server(s) we want to manage, and then create the Data Collection Rule (DCR) to define the type of information to retrieve.
In this scenario, the Data Collection Rule needed to retrieve our events must be created for the specific scope – for this article, I chose to retrieve the logs of Parallels Remote Application Server. The advice is always the same, which is to use a Naming Convention capable of linking objects together and having a name relevant to the scope to be achieved.
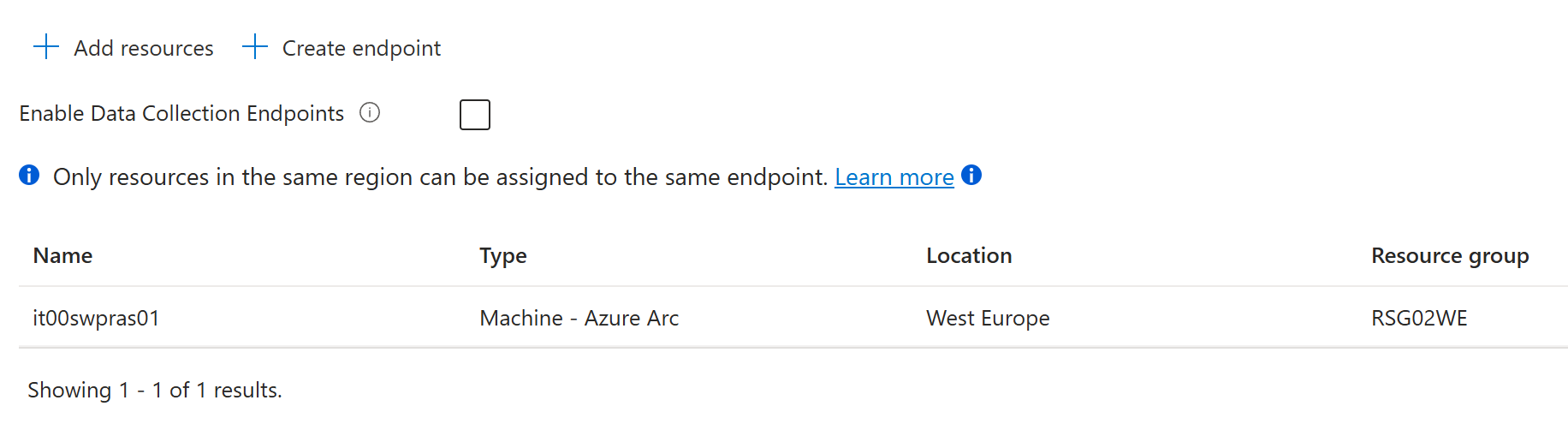
After setting the Basic information, move on to the Resources section where you need to select which servers you want to apply the rule to.
Moving on to the Collect and Delivery section, you will need to configure the Data Source to tap into the necessary information. The type will be Windows Event Logs, while the mode will be Custom.
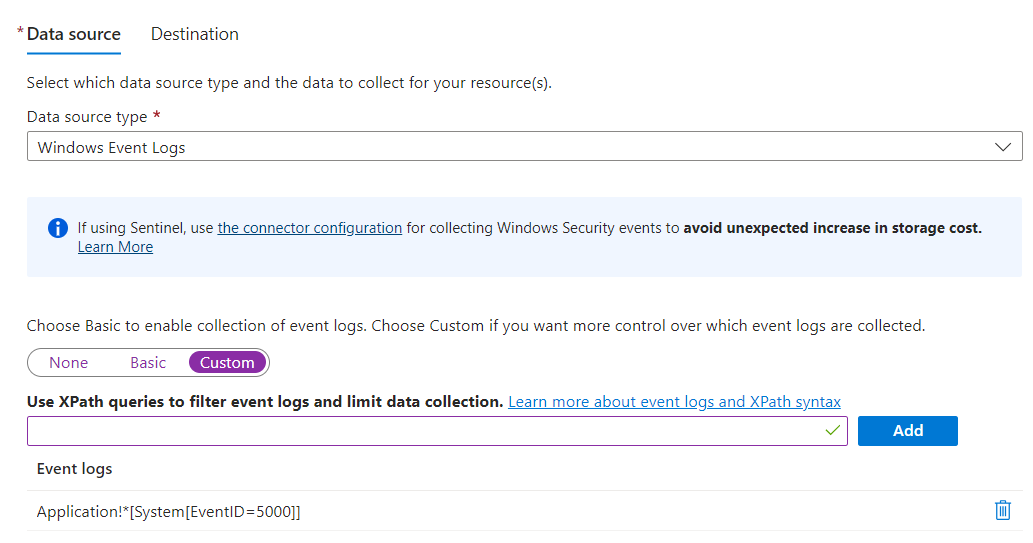
For this scenario, needing to retrieve Application type logs for event 5000, you will need to use the following syntax: Application!*[System[EventID=5000]]
But how do I know the syntax to enter? Through the Windows event viewer, create a filter with the type of events you want to collect.
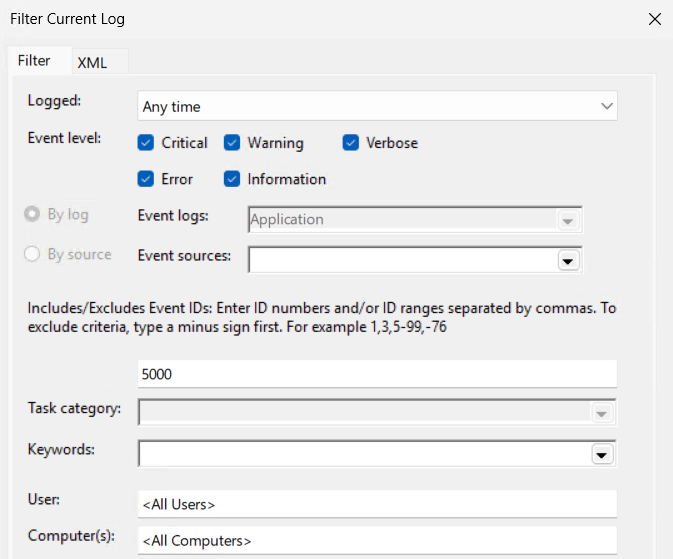
Then go to the XML tab to view the XPath format.
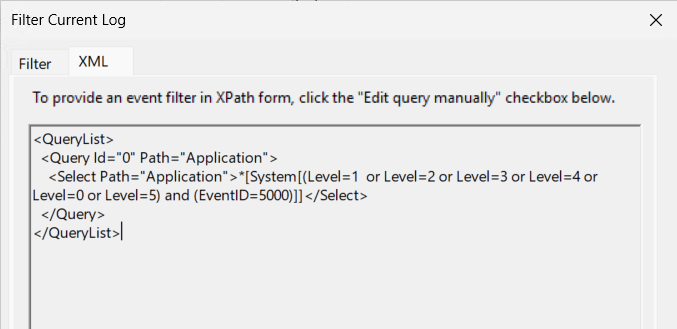
Compared to the syntax written earlier, there is no distinction between Warning, Critical, or Information events, precisely because the wildcard character aims to take everything, but this does not prevent you from collecting only Critical or Error events.
For more information on how to build the syntax, you can refer to the following link – Collect Windows events from virtual machines with Azure Monitor Agent – Azure Monitor | Microsoft Learn.
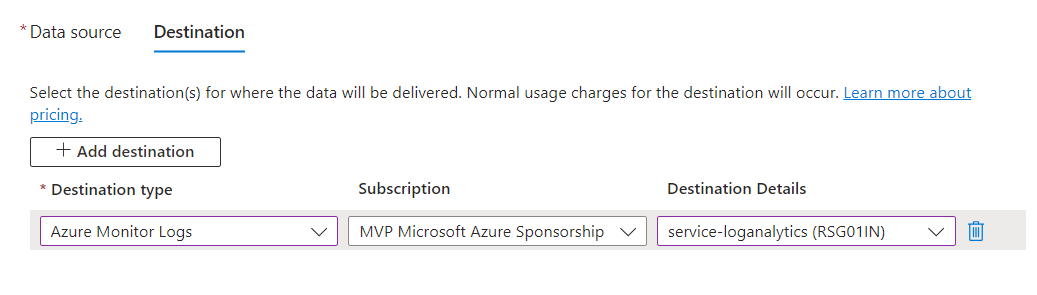
Last but not least is choosing the Destination where to place our logs, which is the Log Analytics Workspace.
Query
After waiting about 20 minutes, you will be able to run a query using this KQL: Event | where EventID == “5000” – which will return a result like this.
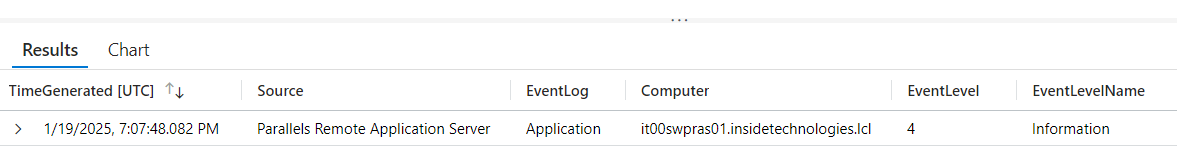
As always, the visualization can be placed within an Azure Workbook or intercepted by a Microsoft Sentinel Analytics Rule to raise a security issue.
Conclusions
The flexibility of Data Collection Rules, thanks to Azure Arc, allows us to retrieve any type of information within our servers, to use the cloud as a complete auditing and compliance tool.
#DBS