What a Friday! I had many cases in my life but this….was amazing. This is the full history with details and the gran finale.
On Friday morning, one of my customer call me (10AM) to advise that all of his clients were strange where “strange” means the disappear of icons from Taskbar, Desktop and Start Menu. The issues were notify by other customers in few hours.
After a faster investigation I found the issue around Windows Defender and in particular with Attack Surface Reduction (ASR) rule “Block Win32 API calls from Office macro”. The details from Windows Security was like this image
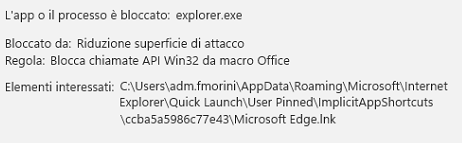
These detections resulted in the deletion of certain Windows shortcut (.lnk) files that matched the incorrect detection pattern. Even I try to change the settings from Block to Audit, nothing changed. The suspect behind the signature was too much strong in my mind because nothing changed and the same behavior happened in many scenarios. Theguilty signature was 1.381.2140.0.
After few hours of first notification, Microsoft has published MO497128 details on this Microsoft 365 Suits category. Microsoft acknowledges that the issue is because of the defender def update issue.
The First Workaround
The first workaround was to to set the rule 92e97fa1-2edf-4476-bdd6-9dd0b4dddc7b from 1 (Enable) to 2 (Audit mode) in case of GPO.
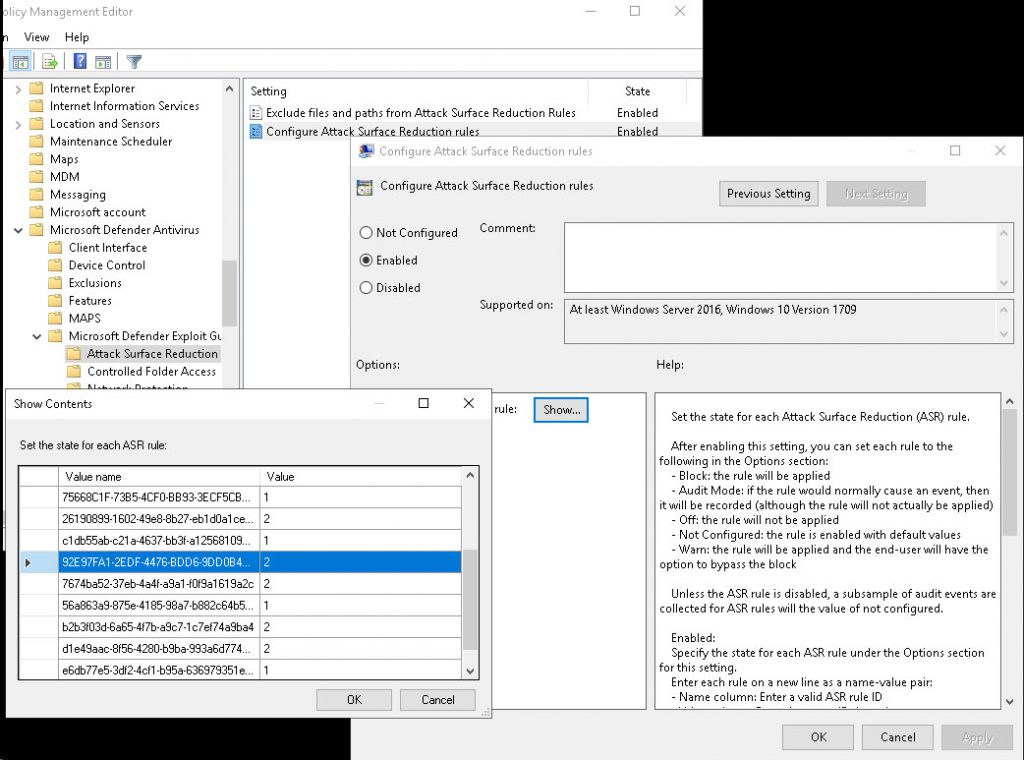
and change the Block Win32 API calls from Office macros setting to Audit for clients managed via Intune.
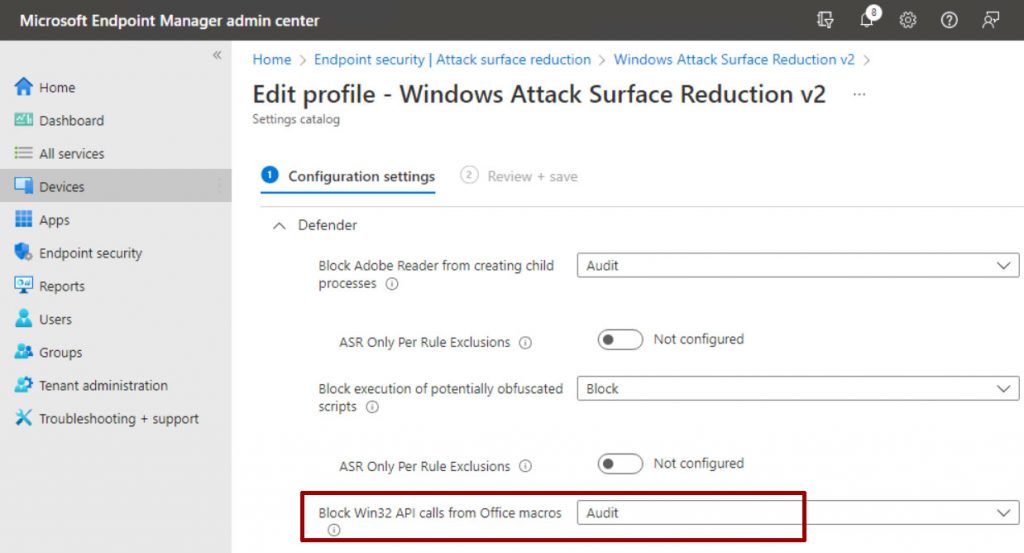
Good but not changed the icon drops. After 5 hours, the security team has published a new signature (1.381.2152.0) that was a rollback.

But the issue was not completely fixed and Microsoft reports to keep the policy in Audit Mode.
The Final Solution
During the night a new a build 1.381.2164.0 that fix the issue even the policy was set to Block or Warn.
What Happen to Icons
Gone! There’s no way to restore the icon but there’s a way to rebuild the most common to Start Menu and to do this, you can use my script available at this link – InsideTechnologiesSrl/DefenderBug: This repository is to save the different solution to restore links after KB2267602 (github.com). I will keep updated the script every day.
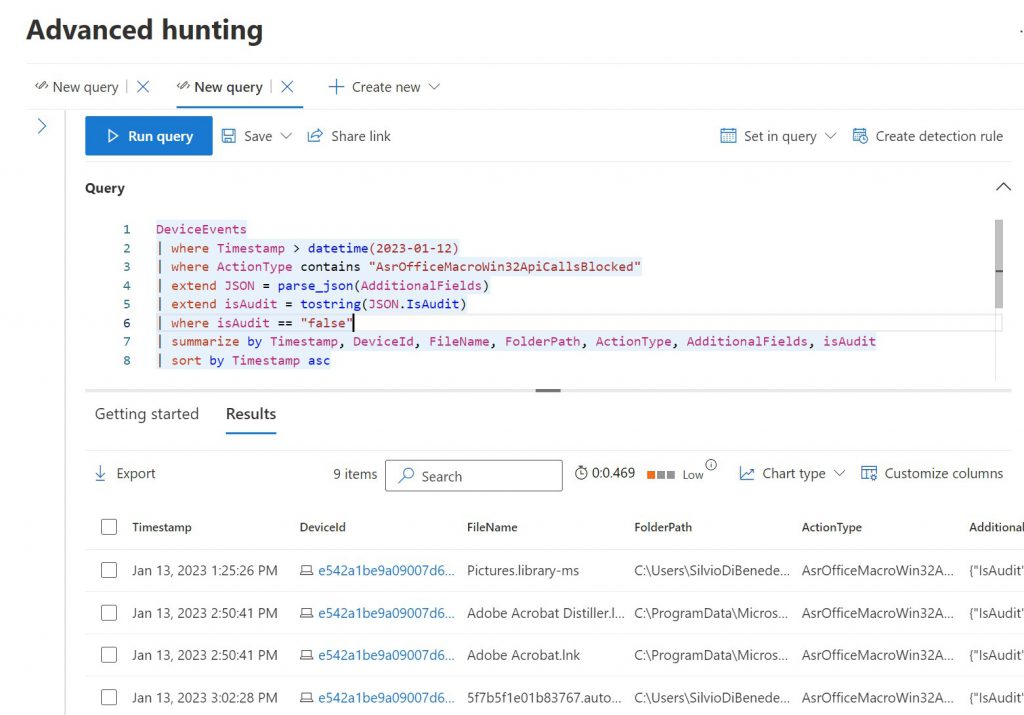
Ok but how I know what icons are deleted? This query from Microsoft Defender 365 Advanced Hunting, can be helpful:
DeviceEvents
| where Timestamp >= datetime(2023-01-13) and Timestamp < datetime(2023-01-14)
| where ActionType contains "BrowserLaunchedToOpenUrl"
| where RemoteUrl endswith ".lnk"
| where RemoteUrl contains "start menu"
| summarize by Timestamp, DeviceName, DeviceId, RemoteUrl,ActionType
| sort by Timestamp asc
The first query generate a detailed report but there are some duplicates for application. With this query the result is a little bit cleaner:
DeviceEvents
| where Timestamp >= datetime(2023-01-13) and Timestamp < datetime(2023-01-14)
| where ActionType contains "BrowserLaunchedToOpenUrl"
| where RemoteUrl endswith ".lnk"
| where RemoteUrl contains "start menu"
| distinct DeviceName, RemoteUrl,ActionType
| sort by RemoteUrl asc
Oh but there’s a script from Microsoft!
Yes but is based on mine script without log status….much easier with the same result.
And Now?
Everything is return to back and you can re-enable the policy but the problem was big and not only for the impact and the reputation but because there will be a huge effort from IT Department to restore icons.
Blame on Microsoft?
Yes and no. Yes because they should test better each update before public release. Yes because rebuild all the icons will be an amazing effort for Help Desk and probably the full restore will require hours and hours. No because this not a critical problem, compared other situation where EDR software deleted files and folders without control. An icon is “important” but is not fundamental for business.
#DBS