In a previous article I’m talked about security and how to disable legacy protocols like TLS 1.0 and TLS 1.1, in order to make our servers / clients more resistant to potential attacks.
Clearly, the elimination of old standards calls for new ones and in fact in 2018, the Internet Engineering Task Force (IETF) formalized the TLS 1.3 standard, 10 years after the arrival of the TLS 1.2. For those unfamiliar with the IETF, it is an open international community of network designers, operators, suppliers and researchers who deal with the evolution of the architecture and proper functioning of the Internet.
Why a new standard has been reached is easy to explain: everything passes from the web, the vulnerabilities research is always on-top of hackers mind and more and more personal data are moved from one server to another around the world. So the idea to find something stronger was mandatory, even if it will take time for the whole world to adapt.
TLS 1.3
Transportation Layer Security (TLS) 1.3 protocol offers unprecedented privacy and performance over previous versions of TLS and unsecured HTTP.
About performance, the goal of TLS 1.3 is to reduce the various operational phases, making the user experience more pleasant (it is no secret that HTTPS connections are slower than HTTP ones), significantly reducing the loading times of the pages for mobile devices and more.
Comparison
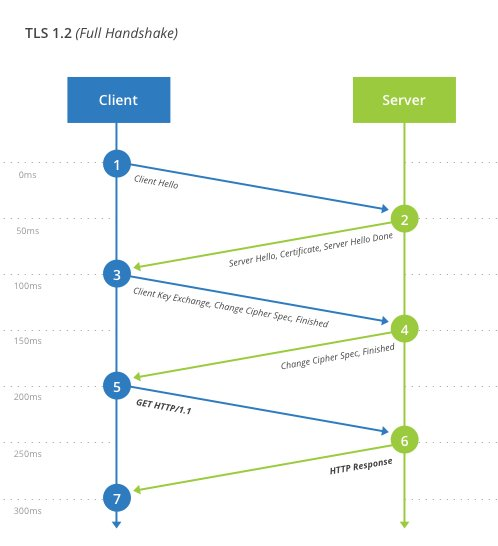
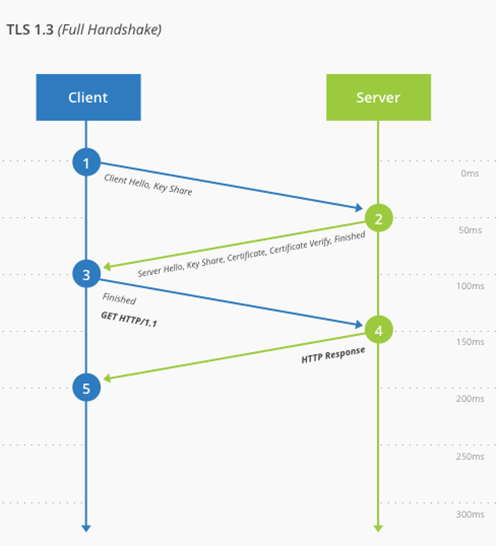
This is a quick comparison of how a connection happens today in TLS 1.2 and how it happens in TLS 1.3; you can immediately see the loss of some steps that will improve performance but also reduce potential attack points.
Pros and Cons
Ready to implement TLS 1.3? As usual, this must be taken with due calm, because a new standard tends to deprecate, or eliminate, some components and these are the ones that are no longer available:
- Static RSA handshake
- CBC MtE modes
- RC4
- SHA1, MD5
- Compression
- Renegotiation
This means that if your site authenticates via SHA1, it will never work with TLS 1.3. Again we will have these features instead:
- Full handshake signature
- Downgrade protection
- Abbreviated resumption with optional (EC) DHE
- Curves 25519 and 448
Microsoft?
Is Microsoft ready to support TLS 1.3? On the browser side, Edge Chromium is compatible, as well as Chrome and Firefox, with the standard while for the operating system part the 1903 builds, both client and server, support TLS 1.3.
From application front, on-premises and cloud, instead there are no official dates; in October there will be the elimination of support for TLS 1.0 and 1.1 for Office 365 and probably some Azure services will follow the same destiny. Hypothetically, from 2021 we could start to see something new and perhaps the first candidate will be Office 365.
More information on this can be found in this article: Microsoft TLS 1.3 Support Reference
Get Started
If you want to better understand how the standard works, in a technical way, you can do it directly from this article: The Transport Layer Security (TLS) Protocol Version 1.3 ′ to Proposed Standard






