Questo articolo è disponibile anche in lingua italiana al seguente link: Attack Surface Reduction: cos’è e come configurarlo al meglio | WindowServer.it
Attack Surface Reduction (ASR) are rules that are part of Windows Defender Exploit Guard that block certain processes and activities, with the aim of limiting risks and helping to protect your organization.
Attacks can be malicious, present in classic executables or hidden in Office or PDF documents, not to mention processes that could be executed by websites. An example of abnormal behavior could be:
- Launching executables and scripts that attempt to download or execute files
- Execution of obfuscated or otherwise suspicious scripts
- Execute commands that apps don’t usually launch during normal daily work
But sometimes, this “potential” risk are present in applications considered “trusts”. However, these behaviors are considered risky because they are commonly abused by attackers via malware.
Unlike Windows Defender Exploit Guard, ASR checks are simple toggle options that administrators can enable/disable with GPOs or through Microsoft Endpoint Manager / Configuration Manager. These rules can also be set in Audit Mode, to generate alerts within the Windows Event Viewer.
ASR functions are available in:
- Windows 10 Pro v1709 or later
- Windows 10 Enterprise v1709 or later
- Windows Server v1803 (Semi-Annual Channel) or later
- Windows Server 2019
With Windows 10 Pro, not all reporting and monitoring features are available but security features are still available.
Figure 1 shows some of the services / processes that can be managed with ASR to date.
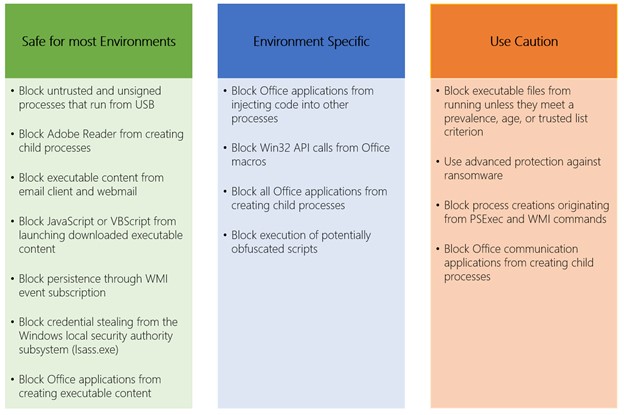
In this article we will not talk too much about this solution on the implementation side, because the Microsoft documentation is complete, when about how to deal with the rules to avoid problems in the productivity field.
ASR configuration via MEM
Like other security settings, ASR is also manageable within the Endpoint Security part of Microsoft Endpoint Manager – figure 2.
Figure 3 and 4 show how to create a new profile and a classic configuration that allows you to better protect a production scenario.
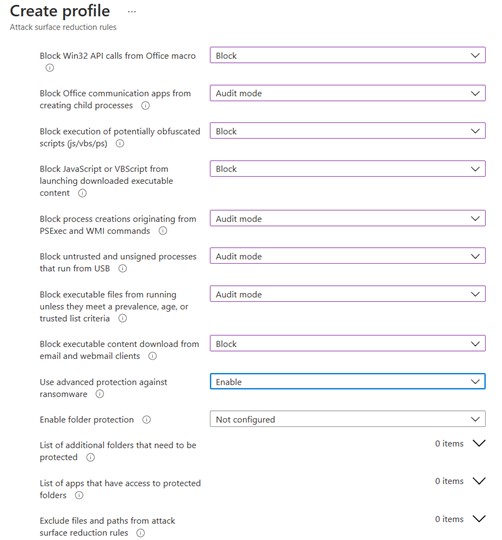
ASR configuration via GPO
With GPOs, in an Active Directory scenario, the configuration of ASR rules is more complex but more complete. It starts with the updated ADMX templates for Windows 10 (Download Administrative Templates), which contain the various parameters to configure Microsoft Defender in the best way.
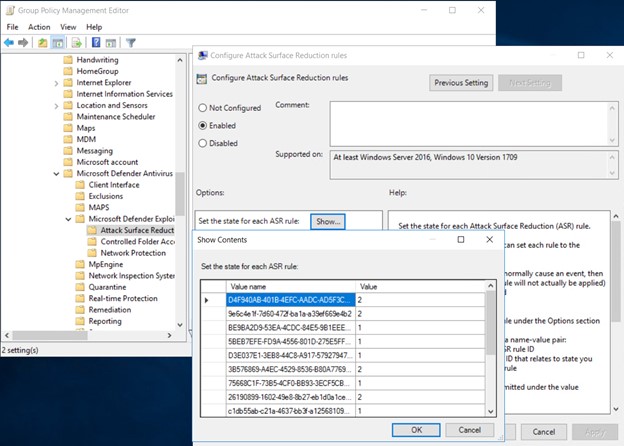
Differently from what happens with Endpoint Manager, the rules must be entered manually with their GUID, using the values 0,1,2 to allow, block or audit. The rules can be retrieved from the Microsoft site – Use attack surface reduction rules to prevent malware infection | Microsoft Docs
NB: not all values are available in Microsoft Endpoint Manager or Configuration Manager, so read the documentation carefully.
Warn Mode
The Warn Mode, is a hybrid between blocking and auditing and allows you to receive a graphical message about what is blocked (in Windows notifications area) but is not supported in all rules and is not always supported yet in Microsoft Endpoint Manager. Among these rules, we find:
- Block JavaScript or VBScript from launching downloaded executable content
- Block persistence through WMI event subscription
- Use advanced protection against ransomware
From Field
The first suggestion that you must create a pilot environment to understand what is blocked and what kind of impact it can have on productivity. It is possible that blocking everything immediately does not lead to no problems, but this is practically impossible.
Let’s see some rules to deal with with white gloves:
- Block process creations originating from PSExec and WMI commands rule – this rule must never be activated if you are using Microsoft Endpoint Configuration Manager (aka SCCM)
- Block untrusted and unsigned processes that run from USB – this rule should not be activated if you have Token keys with software on board
- Block Office communication applications from creating child processes – this rule should not be activated if Outlook calls or needs to interact with third-party plugins (eg Barracuda Archiver)
- Block credential stealing from the Windows local security authority subsystem (lsass.exe) – this rule should instead be used with great caution because it is capable of blocking various processes including Edge updates
The test environment also helps manage path/file exceptions that can be configured via GPO or MEM. It is also possible to create different block profiles for the various users or departments, in order to streamline the overall management. Beware that path / process exceptions are not always supported as in the case of the Block JavaScript or VBScript from launching downloaded executable content or the Block persistence through WMI event subscription.
Another element to keep under control is the SmartScreen for apps and files, which is not connected to ASR but which could block processes in a preventive way. For example, the web portals that must use Tokens on Smart Cards, and that must communicate with local executables, could be blocked by this service.
Analysis
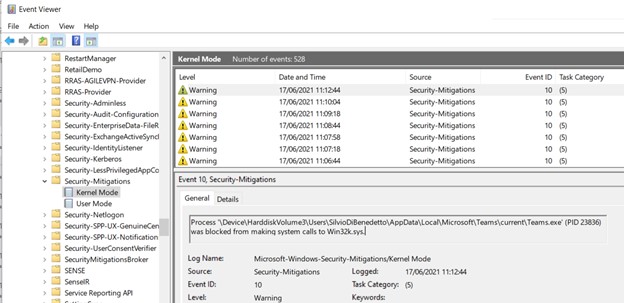
To check if there are any blocks, you can use the Windows event viewer (Security-Mitigations and Windows Defender)
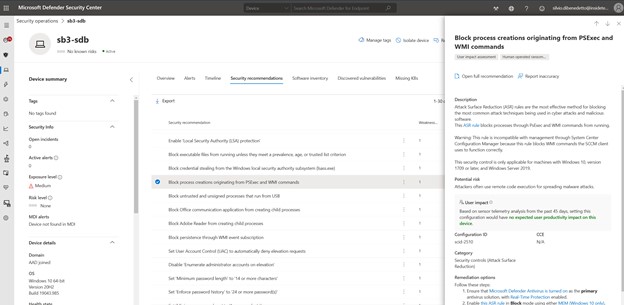
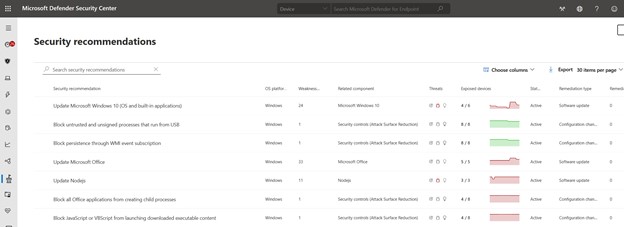
Or through the Microsoft Defender for Endpoint console, which helps us understand what’s going on.
Licensing
As mentioned above, the basic rules can also be used in the Professional version of Windows 10 but using the Enterprise version it is possible to have more functions. Using the E5 license you can use activate Defender for Endpoint and therefore benefit from alerts, real-time monitoring and many others in the reporting field.
Conclusions
Attack Surface Reduction is certainly a tool that must be implemented within your organization, but doing it in the right way leads this system not to create disservices or block daily productivity.
#DBS