Questo articolo è disponibile anche in lingua italiana al seguente link: Azure Arc & Log Analytics: raccogliere i log da Veeam Backup & Replication – WindowServer.it
In a previous article – How to collect and manage audit log with Azure Arc and Microsoft Sentinel – we saw how to activate log capture via Azure Arc. Today we will go into a little more detail, seeing how we can correctly analyze the logs coming from Veeam Backup & Replication.
Before you can get started, you must have already done the following:
- Install Azure Arc on a Linux machine with forward
- Enable syslog into Veeam Backup & Replication
- Create a Data Rule Collections linked to the Linux machine
Configure Linux rsyslog
Azure Arc allows you to collect logs from a Windows and Linux machine, all of which are on your device without the possibility of installing this agent, which is possible to use a link on a Linux machine to enable rsyslog input on the back of Log Analytics. How much machine bridge sound is needed in my infrastructure? Depending on the functionality of your infrastructure, it also depends on the generation of logs.
I pass to configure your reports in the following article – Collect Syslog events with Azure Monitor Agent – Azure Monitor | Microsoft Learn
Configure Veeam
Veeam Backup & Replication v12.1 has introduced native integration with SIEM, and it is then collected in a centralized repository, and the event is managed by the management of the file. Whichever way this “integration” is done, it will be connected to events written in Windows and entered into a syslog in an RFC 5424 format.
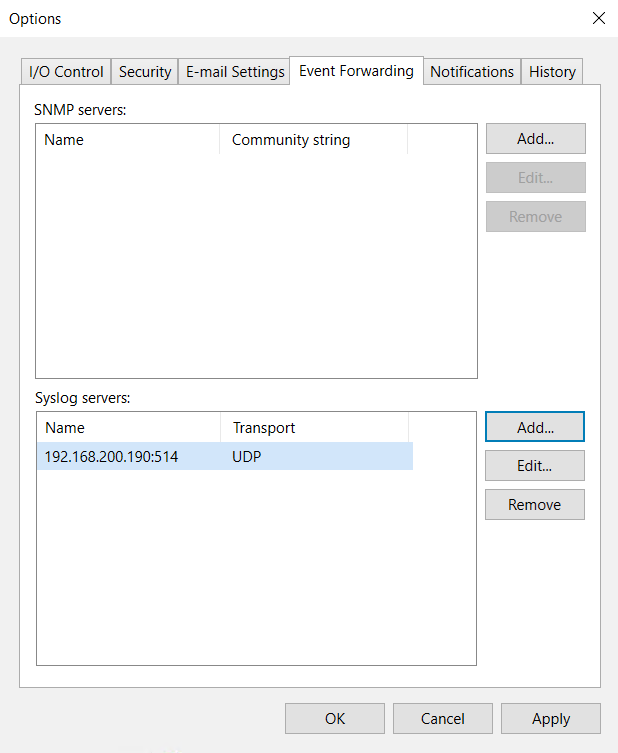
Some key aspects of SIEM integration with backup include monitoring backup-related events, correlating data to more efficiently identify threats or security breaches related to backup operations, and implementing real-time alerts for suspicious activity or unusual backup-related issues.
It is also true that Veeam ONE allows you to have alerts on non-standard behavior of the backup component, but through a SIEM it is possible to implement more extensive protection policies, exploiting the SOAR logic – which could allow us to isolate the server or isolate those is carrying out the malicious operation remotely.
For those who do not yet have a SIEM or do not use Log Analytics, it is possible to make queries in PowerShell, as reported in this article of ours – Veeam Backup & Replication: Audit Administrator Activities.
Configure Log Analytics
Saving logs in Log Analytics, being able to build views of what is being done, having an area where you can view administrator activities and, if desired, generate alarms on potential problems (perhaps more in terms of security than job failure).
It is important to create a Data Collection Rule that collects the logs relating to Veeam which, at least for now, belong to the Log_User facility.
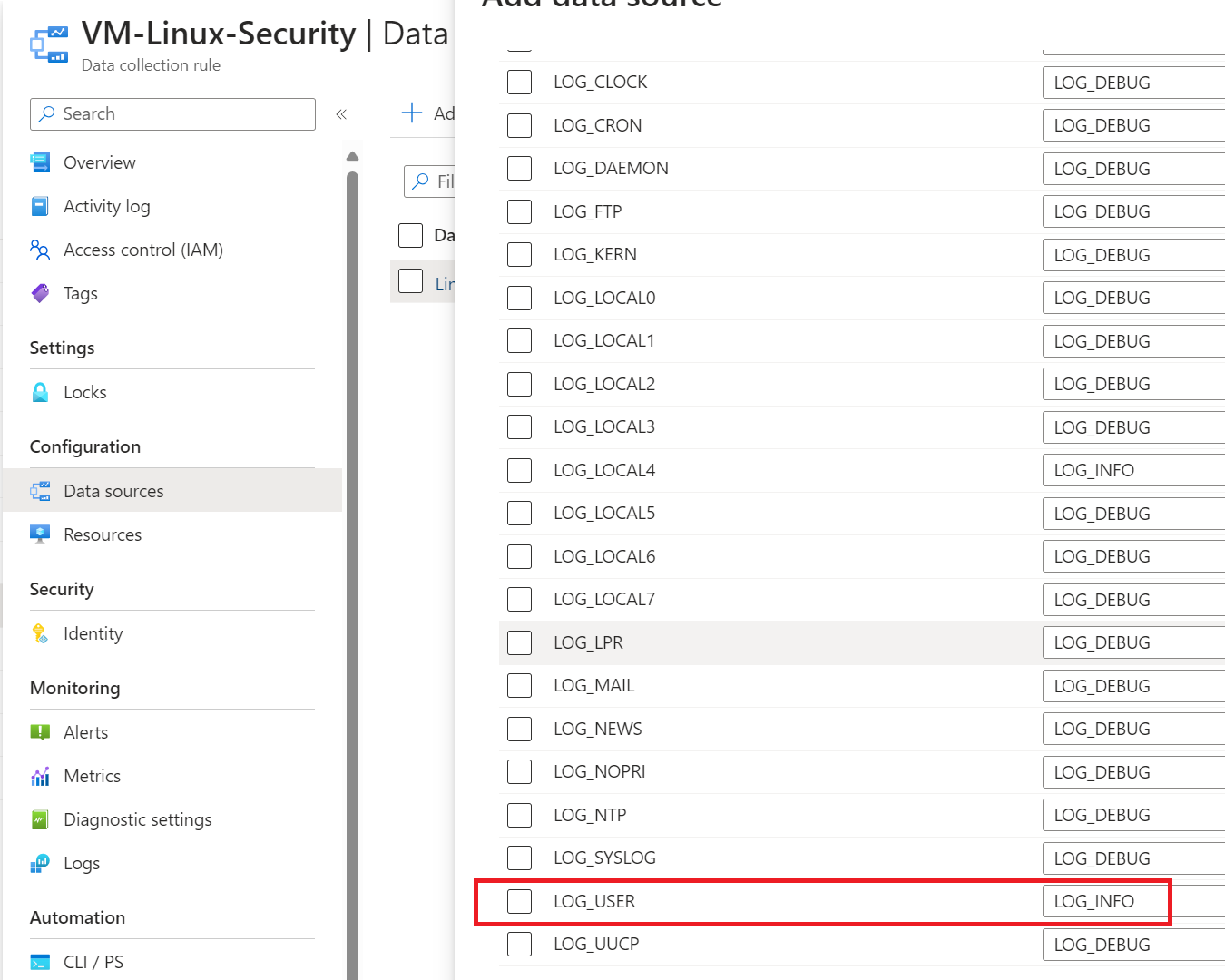
After a few hours have passed since the activation of the DCR, it will be possible to execute queries such as the following: Syslog | where Computer contains “bck01” – remember to change the computer name with your Veeam server.
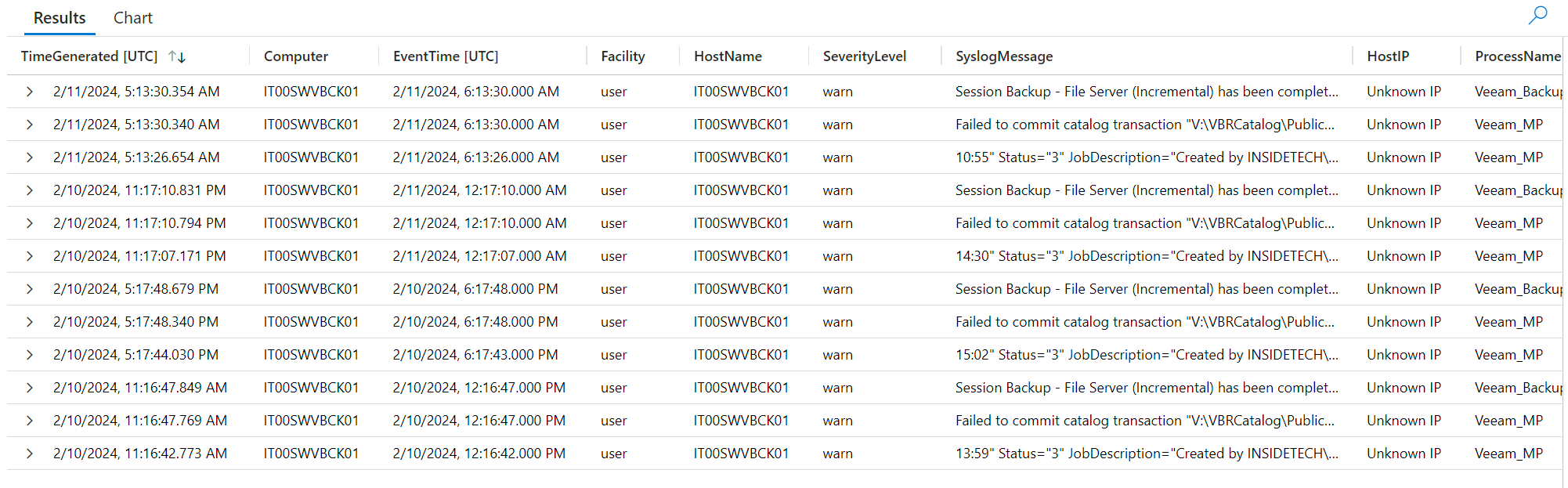
The thing that you immediately notice is that, unlike the Windows world, the class is called Syslog which contains everything related to the Linux world and which can be filtered by the name of the object for which we are interested in recovering the logs.
How can I see only the columns that interest me? After running your query, you can use the Project command to choose the columns you want to display. For example you can use this query: Syslog | where Computer contains “bck01” | project EventTime, SeverityLevel, SyslogMessage, ProcessName
Kusto Query Language Power
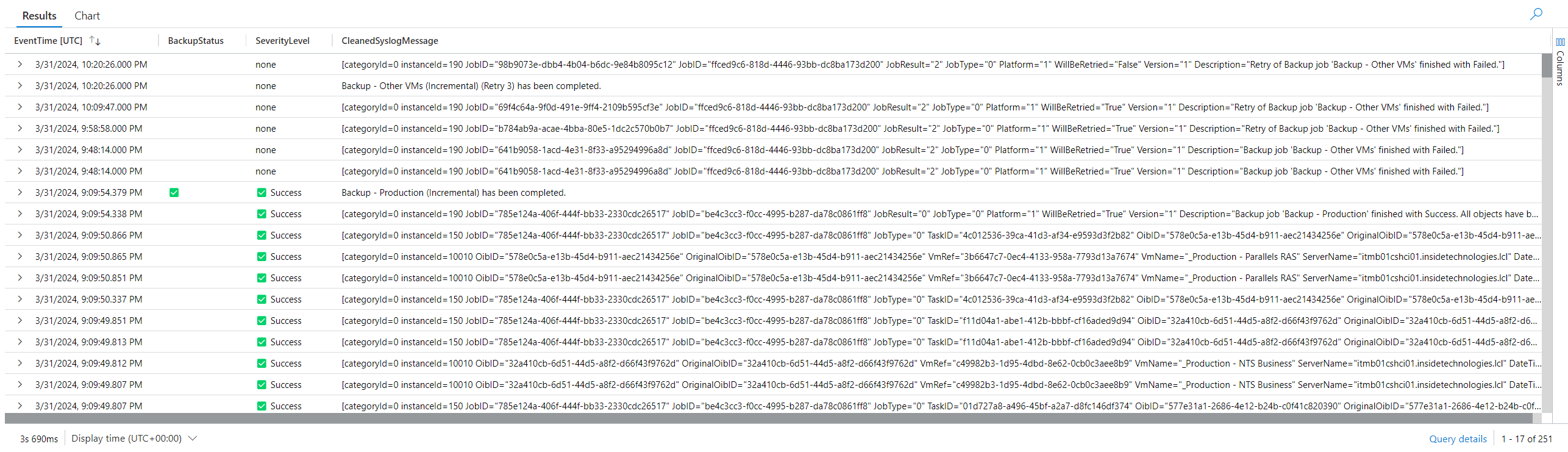
As every time we deal with KQL, we can indulge ourselves in customizing the queries to have a more pleasant graphic appearance. This query concludes what we have covered in this article, with associated customizations in front of icons and columns:
Syslog | where Computer contains “bck01”
| extend BackupStatus = iif(SyslogMessage contains “has been completed” and SeverityLevel == “info”, “✅”,
iif(SyslogMessage contains “has been completed” and SeverityLevel == “warn”, “⚠️”,
iif(SyslogMessage contains “has not been completed” and SeverityLevel == “error”, “❌”, “”)))
| extend SeverityLevel = case(SeverityLevel contains “info”, ‘✅ Success’, SeverityLevel contains “warn”, ‘⚠️ Warning’, SeverityLevel contains “error”, ‘❌ Failure’, ‘none’)
| extend CleanedSyslogMessage = replace(“Session”, “”, SyslogMessage)
| project EventTime, BackupStatus, SeverityLevel, CleanedSyslogMessage
Limits
Using this integration, we still notice the lack of several aspects, such as administrative auditing (who did what) and other information that should be present in a SIEM. These shortcomings, on the Veeam side, will hopefully be filled soon with the next updates.
Conclusions
Azure Arc, integrated with Veeam Backup & Replication, is certainly the ideal solution for monitoring the backups of our infrastructure. The advanced use of KQL helps IT Admins to keep under control all the operations performed by users but also processes and services.