Questo articolo è disponibile anche in lingua italiana al seguente link: Microsoft Endpoint Manager: configurare il Windows Firewall | WindowServer.it
The Cloud-Only scenario is becoming stronger in the client environment, especially for SMEs where many of the services are delegated outside the corporate infrastructure. However, there remains the age-old compliance issue that, in the absence of a Domain Controller and Active Directory infrastructure, can be more complicated than expected.
Microsoft Endpoint Manager (aka Intune) is certainly the perfect tool to achieve this but its logic is very different from Active Directory and what we once did with a click can now take a little more steps.
A classic example is the management of the Windows Firewall and its exceptions. Starting from the main rule that is the firewall must always be active, even in domain environments, there are applications that by default do not configure the various exceptions until they are started or particular functions are called.
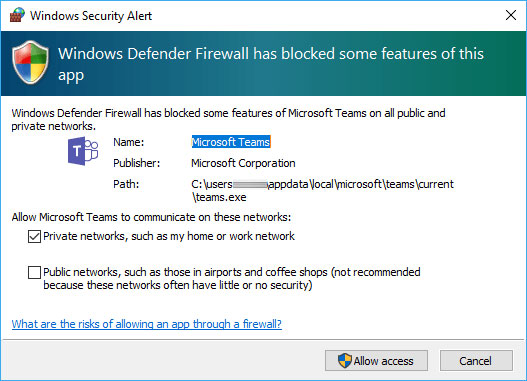
One such software is Microsoft Teams which, during your first meeting or sharing with another user, may show this window – whether you are an administrator of your computer or not.
Policy Configuration
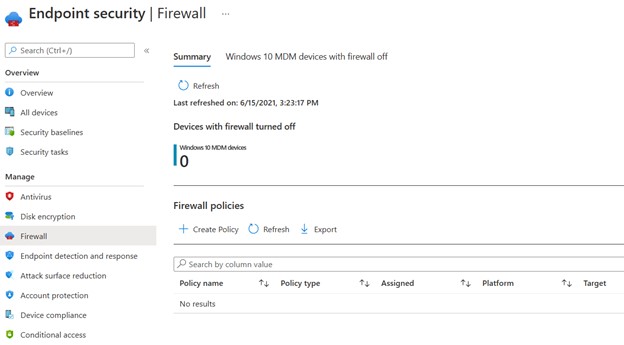
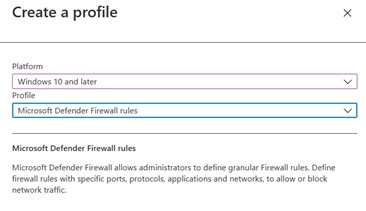
The policy configuration can be centralized from MEM, in the Endpoint Security -> Firewall section – figure 2.
Create a new Windows 10 profile by choosing Microsoft Defender Firewall Rules – figure 3.
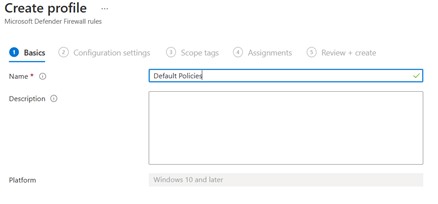
Enter a name and description – figure 4 – and start adding the new rules – figure 5.
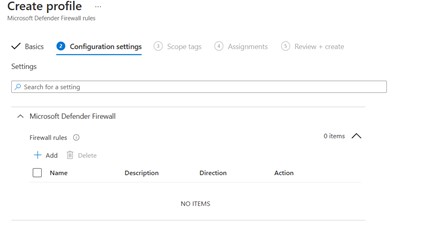
The configuration always includes:
- Name
- Direction (In / Out)
- Action (Allow / Block)
- Network (Domain, Private, Public)
- Application Target (file, service, package – in the case of a UWA)
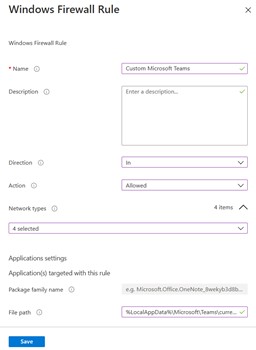
The example in this case is for Microsoft Teams but can also be applied to other products; here are some paths:
- Microsoft Teams: %LocalAppData%\Microsoft\Teams\current\Teams.exe
- Paralles RAS: %ProgramFiles%\Parallels\Client\APPServerClient.exe
- Dike GoSign: %LocalAppData%\infocert\gosign desktop\gosigndesktop.exe
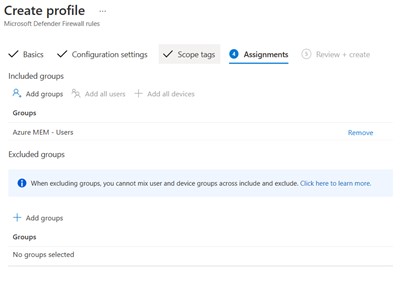
Targeting can be done by users or by device, perhaps using dynamic or assigned groups based on scopes or distributed applications – figure 7.
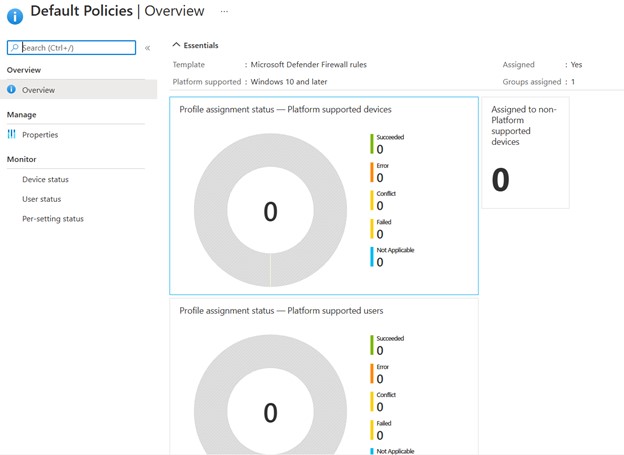
The distribution status will be viewable in the Overview section of each individual profile – figure 8.
Conclusions
With a few steps you can configure the firewall policies even if all the wizards that allow you to enable services such as File Share or Remote WMI – useful in domain scenarios – are still missing.
#DBS