Questo articolo è disponibile anche in lingua italiana al seguente link: Azure Arc: attivare la raccolta dei log dai File Server – WindowServer.it
In a previous article – How to collect and manage audit log with Azure Arc and Microsoft Sentinel – we saw how to activate log capture via Azure Arc. Today we will go into a little more detail, seeing how we can correctly analyze the logs coming from the File Server.
Before you can get started, you must have already done the following:
- Install Azure Arc on File Server
- Create a Data Rule Collections linked to the servers in question and capable of recovering the Security Logs (Success and Failure)
- Enable logs on File Server – Windows File Access Monitoring (netwrix.com)
Analyses
After a few hours have passed since the activation of the DCR, it will be possible to execute queries such as the following: SecurityEvent | where Computer contains “it00swfs01” and Account contains “silvio.dibenedetto” and EventID == “4663” | where TimeGenerated >= ago(6h)
Remember to change the Account variable with the user you want to search for and the Computer variable with the naming convention that contains your File Server, so as to filter only the necessary operations.
How can I see only the columns that interest me? After running your query, you can use the Project command to choose the columns you want to display. For example you can use this query: SecurityEvent | where Computer contains “it00swfs” and Account contains “silvio.dibenedetto” and EventID == “4663” | where TimeGenerated >= ago(6h) | project TimeGenerated, Account, Computer, ObjectType, ObjectName, IpAddress, Activity
Advanced Security Information Model
This is the first way to analyze the data. There is a second one that uses the Advanced Security Information Model, that is a “normalizers” of the saved logs and which allow queries to be made in another way, sometimes having a clearer view, as well as being able to cross-reference sources. These templates are available at the following link – Azure-Sentinel/ASIM at master · Azure/Azure-Sentinel · GitHub.
The templates, in addition to a new query syntax, integrate ready-made Azure Workbooks, which help to carry out the desired analyses. In this case, the scheme is called File Event, while the workbook is called File Event.
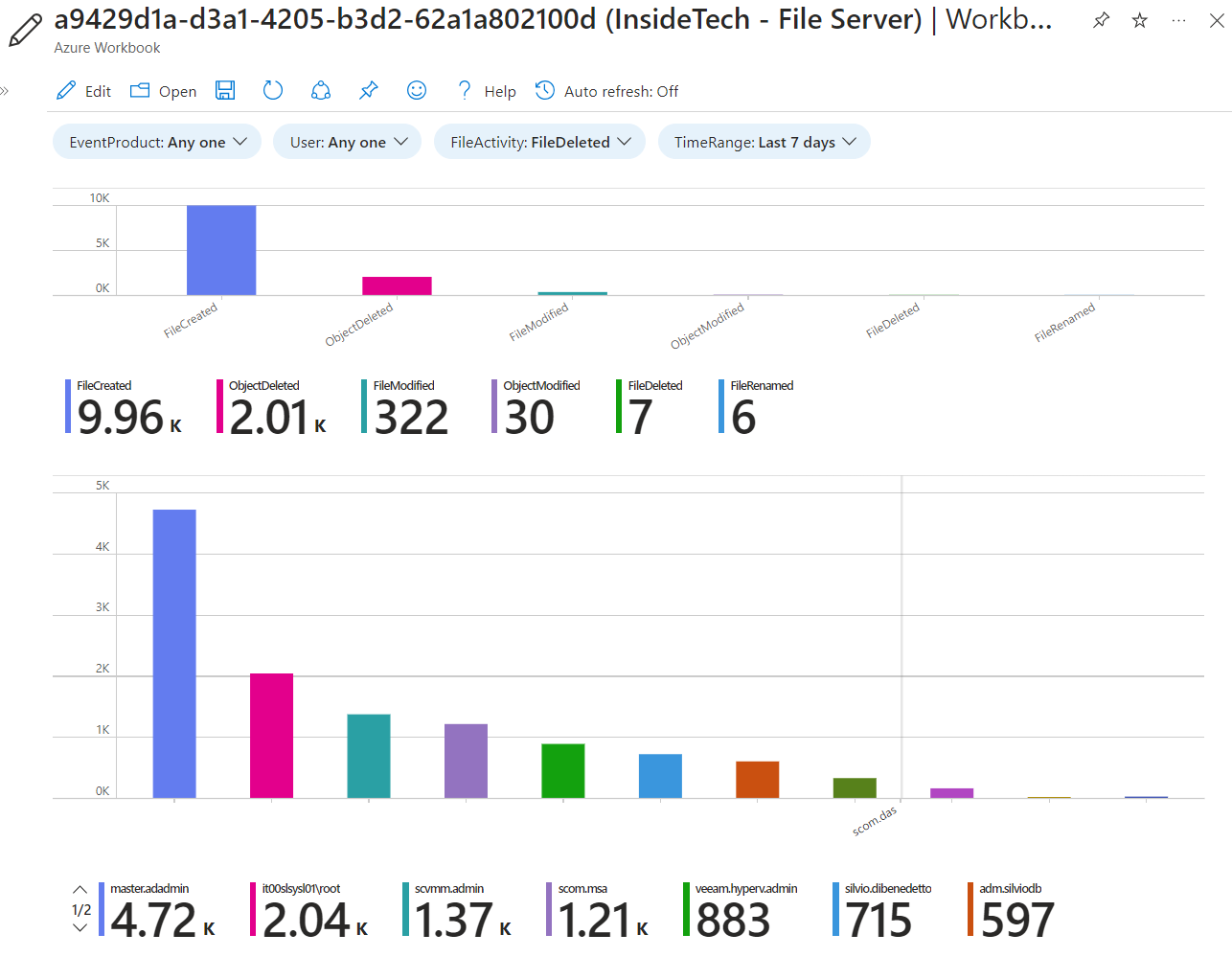
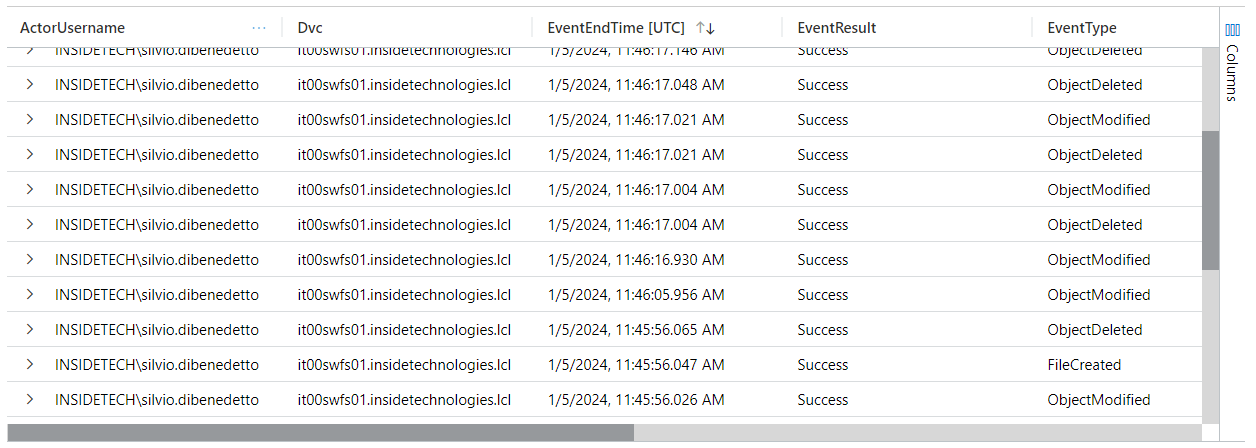
Another advantage of these normalizers is the possibility of querying multiple sources easily. An example is given by this query: imFileEvent | where Dvc contains “it00swfs” and ActorUsername contains “silvio.dibenedetto” | where TimeGenerated >= ago(6h) | project ActorUsername, Dvc, EventEndTime, EventResult, EventType, TargetFileName, FilePath, TargetFilePath, IpAddr
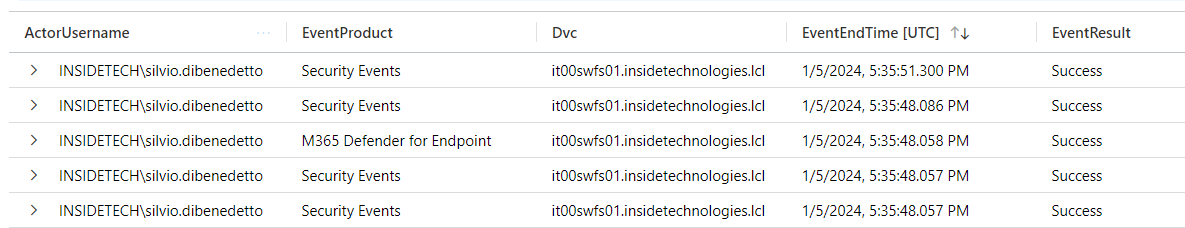
The query is made in Kusto Query Language, where you can see the integration between the various classes but above all the aesthetic modification, and merges the logs coming from the Security part and those from Defender for Endpoint. If you want to learn more about the use of KQLs, you can read this article – Azure Monitor workbook grid visualizations – Azure Monitor | Microsoft Learn.
Integration with Microsoft Defender for Endpoint
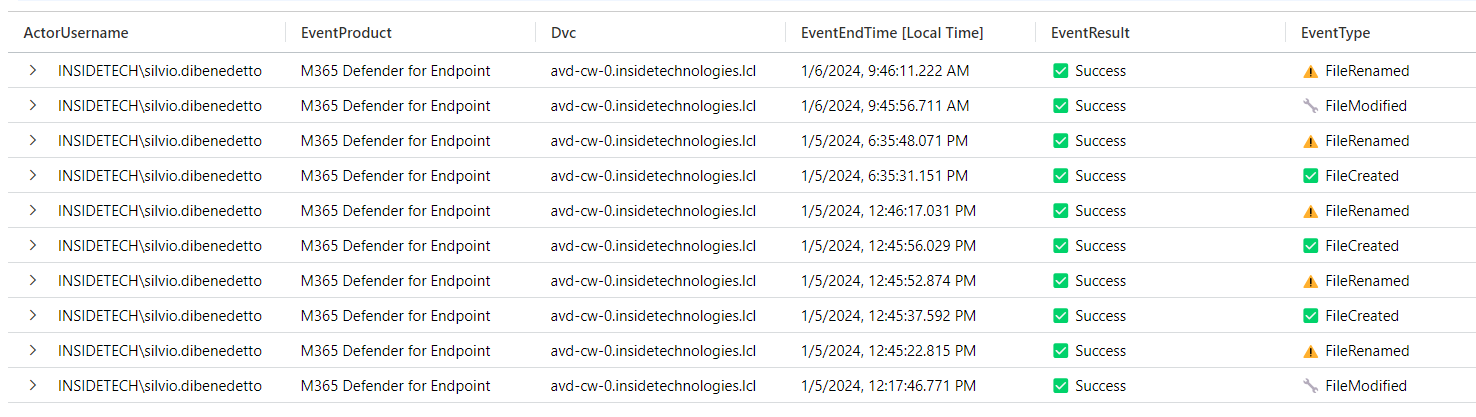
Not everyone knows that the integration between Microsoft Defender for Endpoint and Microsoft Sentinel also brings file modification logs, and more, as shown in the previous image. This offers even more functionality when analyzing. To activate the integration you need to configure the Microsoft Defender XDR Data Connector, choosing the DeviceFileEvents connector.
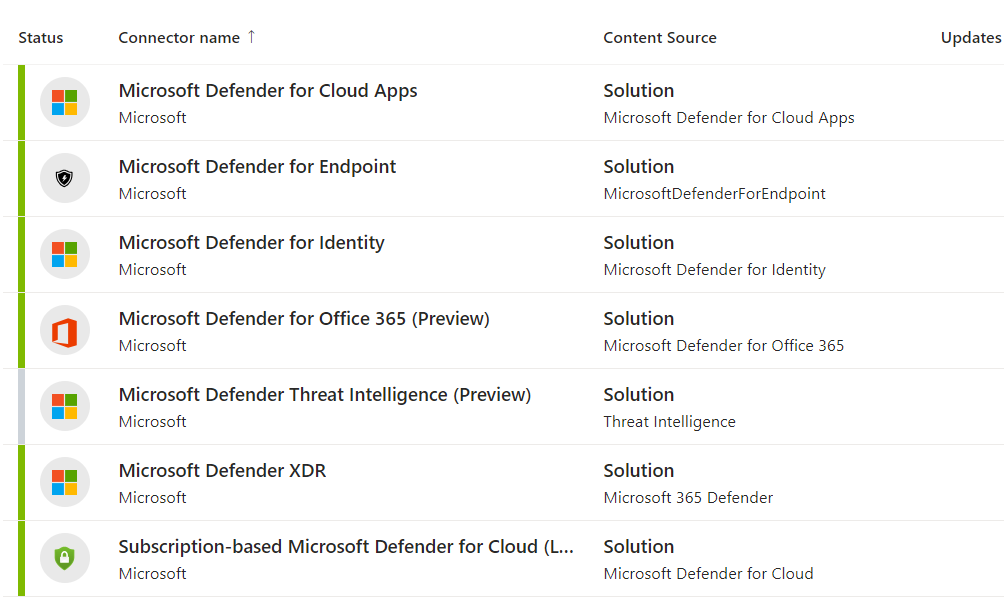
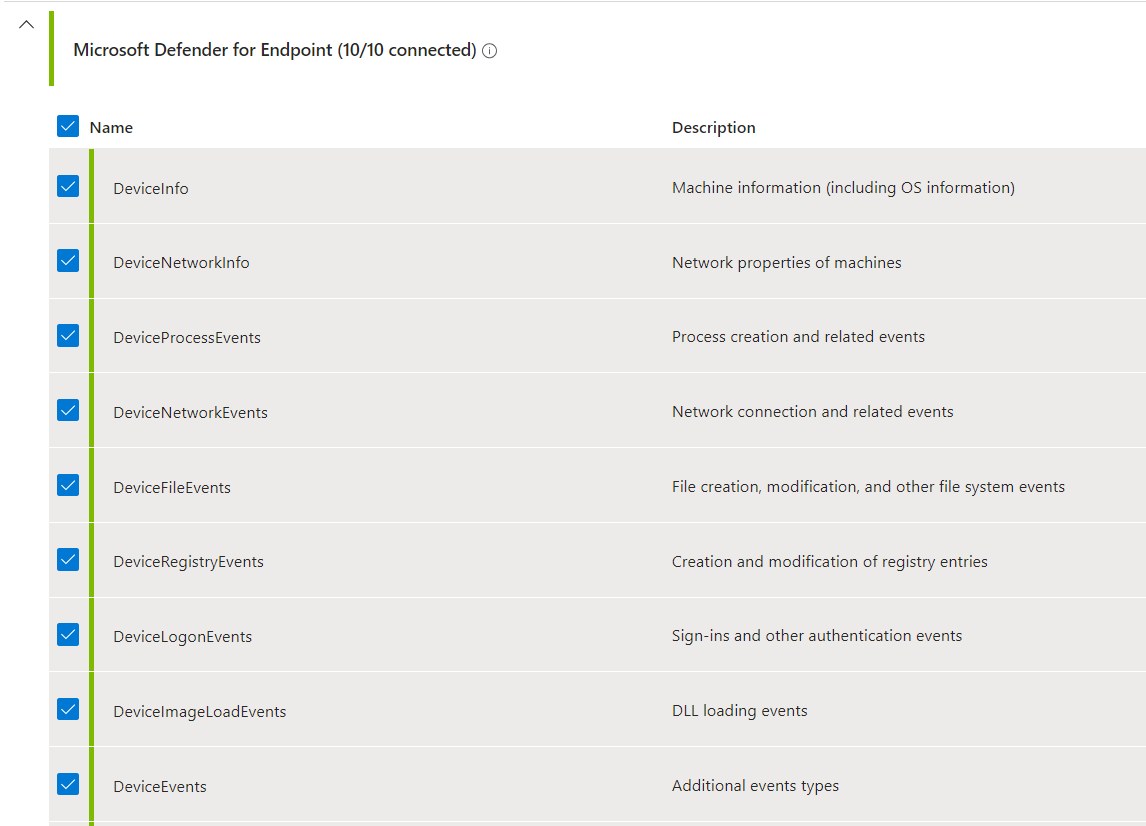
Note: this operation may increase the number of logs acquired and therefore the cost of the Log Analytics Workspace.
Run this query to check how it works: imFileEvent | where Dvc contains “it00swfs” and ActorUserType <> “System” and ActorUserType <> “Service” and ActorUserType <> “Machine” and TargetWindowsUsername !contains “nt autority” and ActorUsername !contains “admin” and TargetFilePath !contains “vhdx” and EventProduct contains “M365” | where TimeGenerated >= ago(24h)
In this case we are using the normalizer to execute a query, retrieving the events generated by the “M365 Defender for EndPoint” product; in detail, the query recovers all the creations/modifications made on the files, excluding service accounts, administrators or machine objects.
This query concludes what we have covered in this article, with associated customizations in front of icons and columns: imFileEvent | where Dvc contains “it00swfs” and ActorUserType <> “System” and ActorUserType <> “Service” and ActorUserType <> “Machine” and TargetWindowsUsername !contains “nt autority” and ActorUsername !contains “admin” and TargetFilePath !contains “vhdx” and EventProduct contains “M365” | where TimeGenerated >= ago(24h)| project ActorUsername, EventProduct, Dvc, EventEndTime, EventResult = case(EventResult contains “Success”, ‘✅ Success’, EventType contains “Failure”, ‘❌ Failure’, ‘none’), EventType = case(EventType contains “FileCreated”, ‘✅ FileCreated’, EventType contains “FileRenamed”, ‘⚠️ FileRenamed’, EventType contains “FileDeleted”, ‘❌ FileDeleted’, ‘none’), TargetFileName, FilePath | order by EventEndTime
Conclusions
Azure Arc, integrated with Microsoft Defender XDR, is certainly the ideal solution for monitoring user activities within Active Directory. The advanced use of KQL helps IT Admins to monitor all the operations performed by users but also by those who have particular privileges within AD.