Questo articolo è disponibile anche in lingua italiana al seguente link: Il danno della Cumulative Update di novembre con il Kerberos – WindowServer.it
Like every second Tuesday of the month, Microsoft has released various updates for its various operating systems and software but this time it has created much greater damage than expected. The Kerberos protocol was affected, which has a very serious impact on the authentication part.
Step back! Where we start? The first week of November, a new vulnerability has been discovered, CVE-2022-37966 (Windows Kerberos RC4-HMAC Elevation of Privilege Vulnerability), with this attach model:
“An unauthenticated attacker could conduct an attack that could leverage cryptographic protocol vulnerabilities in RFC 4757 (Kerberos encryption type RC4-HMAC-MD5) and MS-PAC (Privilege Attribute Certificate Data Structure specification) to bypass security features in a Windows AD environment.”
So Microsoft decide to change some logic behind Kerberos and Netlogon authentication, with a deployment process that will be closed on April 2023. Just to avoid panic, the Cumulative Update create issues only if installed on Domain Controller.
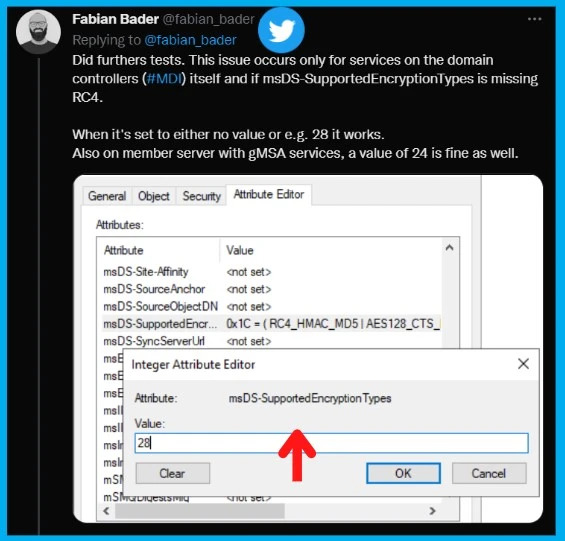
Returning to the Kerberos problem, it seems that the KDC service does not support encryption correctly, unless an attribute is declared in Active Directory – msDS-SupportedEncryptionTypes.
Fabian Bader, Microsoft MVP, posted on Twitter to demonstrate how having a value equal to 24 or 28 solved the problem.
What Software?
- Windows Server 2008 R2 and above
- Windows 10 and 11
- Azure Stack HCI
- Microsoft Configuration Manager
- System Center Operation Manager
- System Center Virtual Machine Manager
- Veeam Backup
Probably the list is much long and is related around Kerberos authentication.
The Solution
Microsoft ran to fix this with the release of a corrective patch, available only from Microsoft Update – therefore to be installed by hand – to add a registry key and therefore solve a serious problem which however does not seem to have affected all users.
The detail of the fix reads:
“Microsoft is releasing Out-of-band (OOB) updates today, November 17, 2022 and November 18, 2022 for installation on all the Domain Controllers (DCs) in affected environments. This update addresses a known issue which might cause sign in failures or other Kerberos authentication issues. You do not need to install any update or make any changes to other servers or client devices in your environment to resolve this issue. If you used any workaround or mitigations for this issue, they are no longer needed, and we recommend you remove them.”
The corrective patch is available at the following link – Windows message center | Microsoft Learn.
Death to Patches?
For those who insist on the philosophy of “I don’t install patches because they cause damage” it is good to remember that having up-to-date software reduces the attack surface, guarantees support from Microsoft (and its partners) but makes you compliant with eyes of the GDPR, in case of proven data breach.
The suggestion is to always wait until the end of the month to understand if problems arise or if your infrastructure is simply part of the scenario potentially at risk.
#DBS