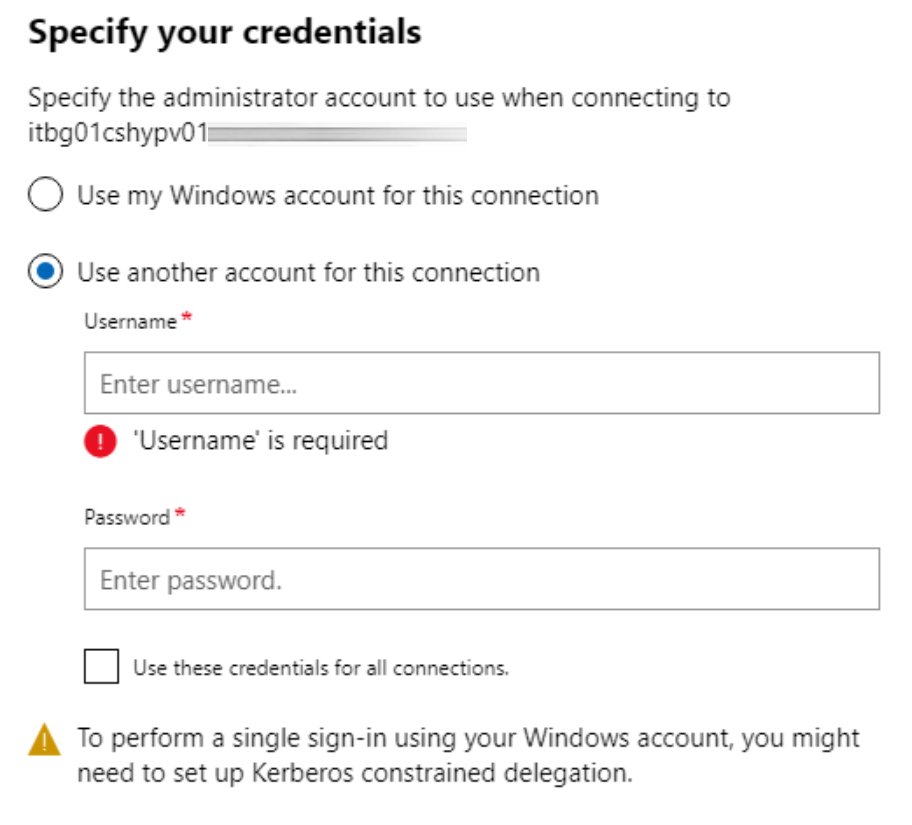
Windows Admin Center needs to be authorized when a user try to connect into a server and this means enable SSO. Without the configuration of a constrained Kerberos delegation, WAC will display an alert that is not possible to connect using the Use my account for this connection option.
To avoid this, is necessary delegate the Windows Admin Center gateway and PowerShell is the perfect tool to achieve the goal. The idea is take all servers from a specific OU, this means change the SearchBase for Domain Controllers. The cmdlet can be run from a Domain Controller or from a management machine where PowerShell ActiveDirectory module is present and, just to be clear, if you have the right permissions to change values in AD.
$ServerList = Get-ADComputer -Filter * -SearchBase “OU=Servers,OU=InsideTech,DC=insidetech,DC=local”
$WAC = “it00swweb01”
foreach($Server in $ServerList){
Set-ADComputer -Identity (Get-ADComputer $Server.Name) -PrincipalsAllowedToDelegateToAccount (Get-ADComputer $WAC)
}
If you want restrict the search, is possible use the filter option to chose all servers start with specific name: Get-ADComputer -Filter ‘Name -like “it00swhy*”‘ – by the way if you want learn more about filter, check this guide: Get-ADComputer from MS Docs.
To verify if the modify has been applied, run the cmdlet Get-ADComputer it00swhypv01 -Properties * | Format-List -Property *delegat*,msDS-AllowedToActOnBehalfOfOtherIdentity and check if the PrincipalsAllowedToDelegateToAccount property display the CN of the Windows Admin Center server.
Done!
Get Started
Download Windows Admin Center!
#DBS