New appointment with Windows Server 2012 R2. Today I will talk about Dynamic Access Control, a feature already present in the 2012 RTM, which allows the management of access to documents in a much more flexible and functional than the old model based on groups.
Before Windows Server 2012 to give the permissions within the shared folders, you used the various Active Directory groups but this forced IT administrators to have a large number of groups and make nests of various kinds to allow access to a particular folder; also when a user changed the department, IT admin was obliged to change the various associations to groups so that could still access the material to him no longer allowed.
Dynamic Access Control makes everything much simpler and relies on the concept of the attributes of AD, which are standard and have the distinction of being flexible. First, create two users in Active Directory, the first must be into Finance department and the country Italy, while the second will be a part only of the Finance department. The management of DAC is made through the new Active Directory Administrative Center, let’s start with create a new Claim, in the section Dynamic Access Control -> Claim Types, as shown in Figure 1.
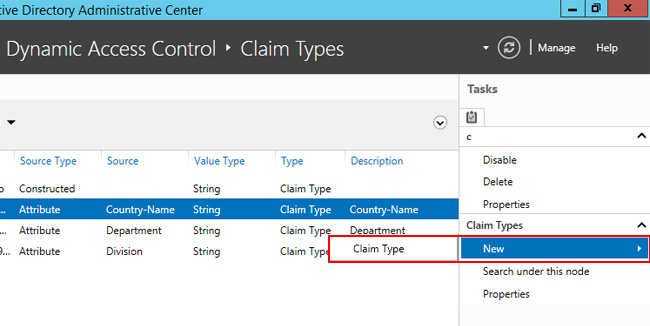
Figure 1 – New Claim
During this demonstration we will use the Claim Country-Name and Department, but you are free to customize it. The Country-Name Claim – Figure 2 – is simply called in AD c, so it is recommended to change the display name so that it is more understandable. Another thing that can be entered are the values suggested by default within the rules.
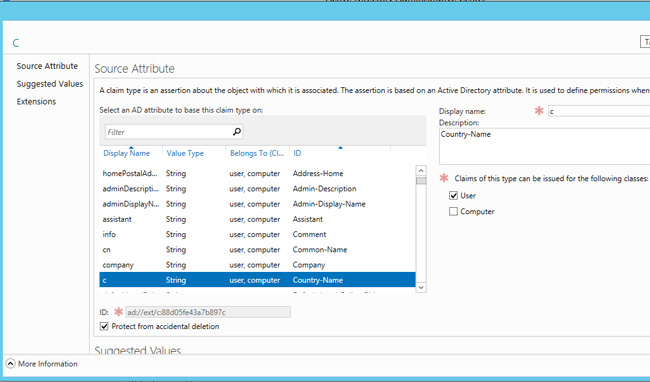
Figure 2 – Claim Country-Name
After entering both the Claim, you must enable and to do this you have to move in the Resource Properties, as shown in Figure 3.
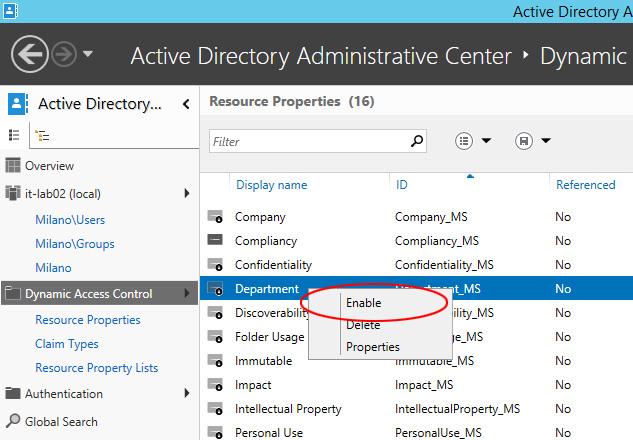
Figure 3 – Enable Claim
At this point you should create a centralized rule, through the Central Access Rules section, as shown in Figure 4.
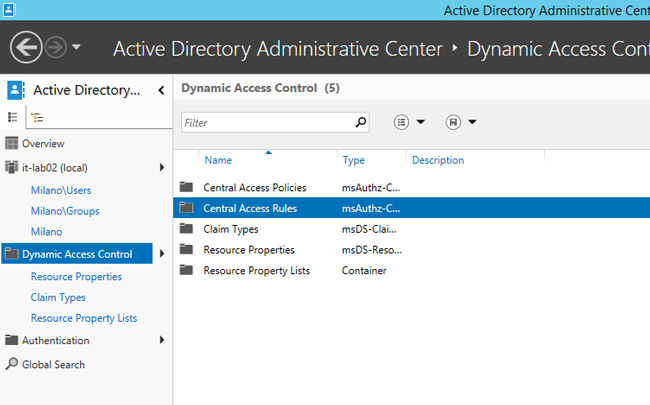
Figure 4 – Central Access Rules
Create a new rule with a name of your choice, and edit the permissions, adding new elements as shown in Figure 5. In this demo you will ensure that all users in the group Finance Admins will have write permissions if they belong to the Finance department and the country Italy. Insert another permission where the same group will have read-only permissions if they belong to the department Finance, without and then specify the country.
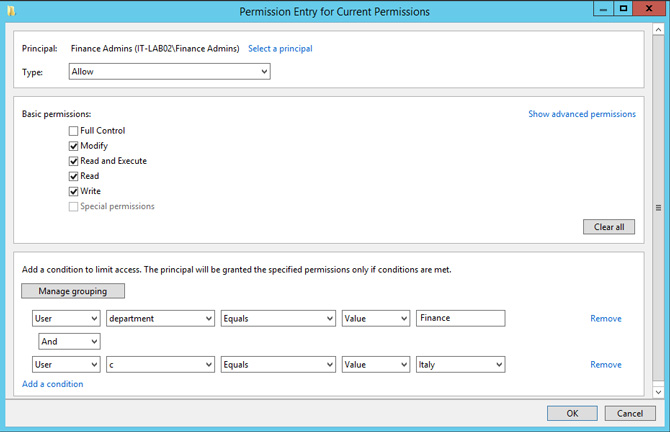
Figure 5 – Creating Permissions
After creating the various Rules will be possible to insert them within the policy, within the section of Central Access Policy, as shown in Figure 6.
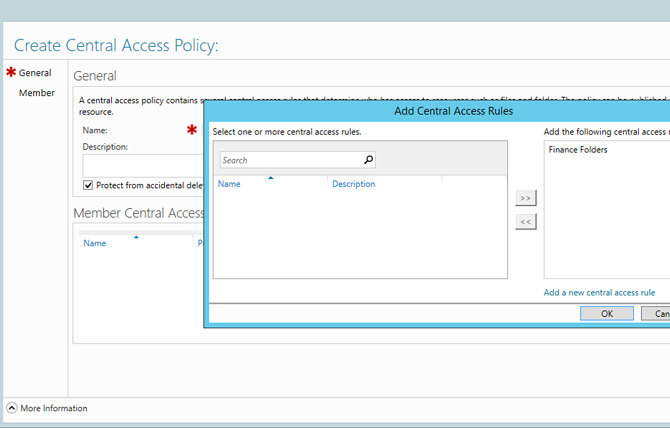
Figure 6 – Central Access Policy
The last step is the creation of a Group Policy that allows the application of the CAP to all File Servers. To do this you need to create a new GPO and edit voice Computer Configuration -> Windows Settings -> Security Settings -> File System, right-click on Central Access Policy and select Manage Central Access Policies, inserting various policy created Figure 7.
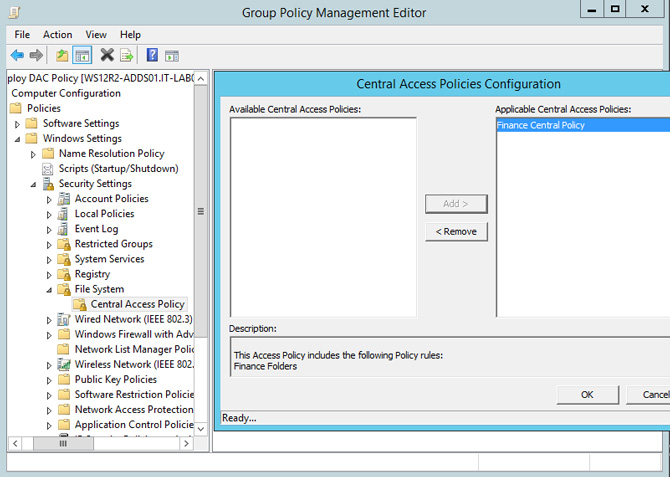
Figure 7 – Select CAP
Now we have to enable Domain Controller to issue Claims to the users and to do this you must activate the policy KDC Support for claims, compound authentication and Kerberos armoring, present in the Default Domain Controllers Policy GPO, in the path Computer Configuration -> Policies -> Administrative Templates – > System -> KDC – figure 8. The policy must be changed to Supported.

Figure 8 – Change KDC GPO
At this point open the File Server and update the policy with gpupdate /force, create a new shared folder. In order to allow DAC permissions to go into play, allow everyone NTFS/Share full control permissions and then DAC will overwrite it, if the user doesn’t have NTFS permissions he will be denied access even if DAC grants him access. Create a new subfolder called Finance and open the advanced properties, go to the Central Policy and assign the rule from CAP, Figure 9, then move on to the client for testing.
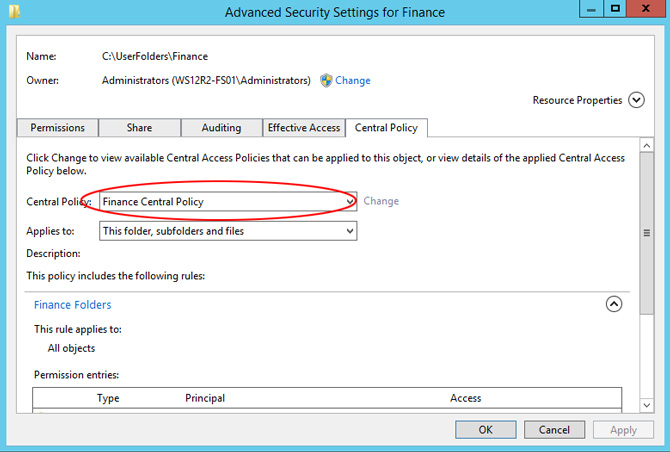
Figure 9 – Application Central Policy
If you did everything correctly, you should be able to create documents with users who belong to the Finance department and the country Italy, while those who belong only to the Finance department can only read the contents.
S




Follow on Socials