Questo articolo è disponibile anche in lingua italiana, al seguente link – Azure Arc: configurare un Linux rsyslog verso Log Analytics – WindowServer.it
New appointment related to Azure Arc, where we will see how the integration of the Linux world works in terms of devices based on proprietary firmware or special software. In this previous article, we saw how to integrate the syslog part of Veeam Backup & Replication into Log Analytics to collect everything done by administrators, as well as the job history.
The question that is often asked is: “How do you configure the bridge machine to transform it into an rsyslog towards Log Analytics?” Before starting, it is worth mentioning that the logic behind the scenes has not changed much, but the old Microsoft Management Agent (MMA), inherited from System Center Operations Manager, was officially deprecated and retired a few months ago to make way for the Azure Monitor Agent (AMA), which offers many more functionalities in terms of granularity, including the use of Data Rule Collection – a topic already covered several times in previous articles.
But why an rsyslog? Because devices like firewalls, switches, and storage do not have the capability to write directly into Log Analytics, needing an agent or integrated APIs to move their logs. Syslog is a universal “standard” that any SIEM platform supports, making it easier to stay in the middle rather than building an adaptation that would then have to be made for all the various vendors on the market.
Installation
The Linux rsyslog machine must be among the SKUs supported by Azure Arc – Connected Machine agent prerequisites – Azure Arc | Microsoft Learn – while the agent installation is the classic one available from the Arc portal.
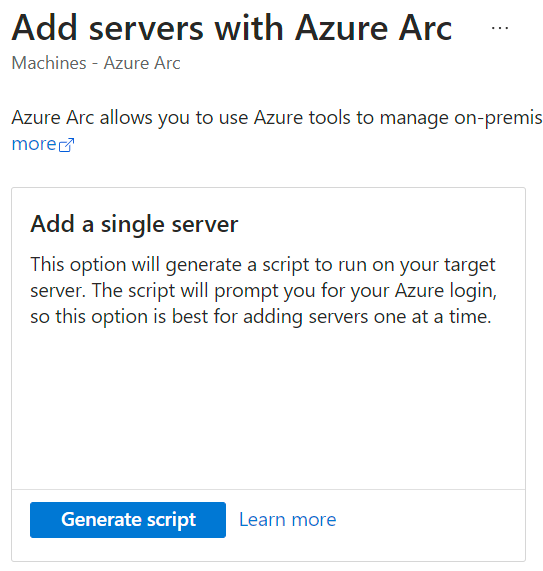
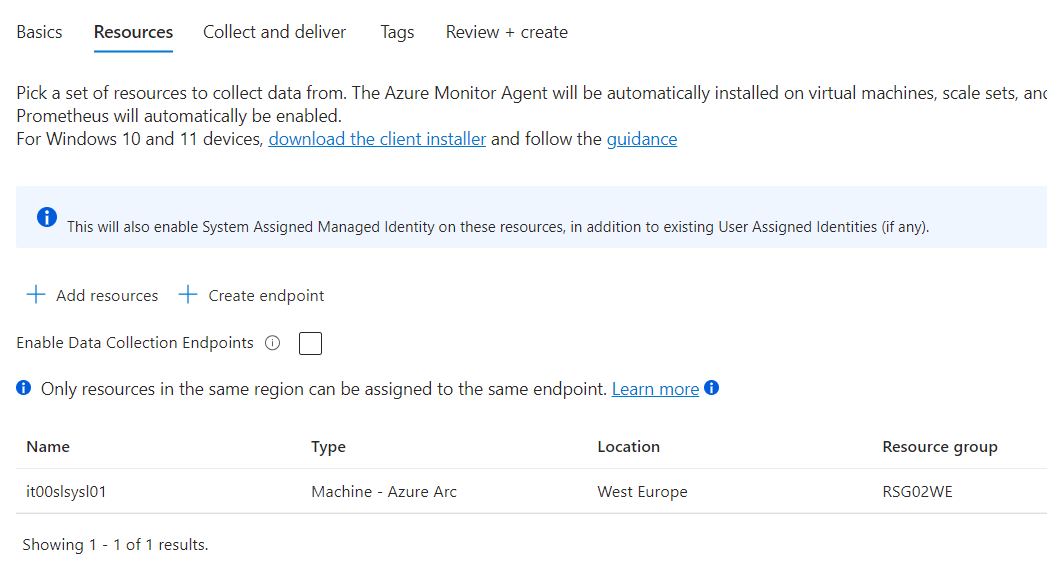
Once the installation is complete and the resource is presented in Azure Arc, it will be possible to create the Data Collection Rules (DCR) necessary to collect the logs we are interested in. For small environments, it is possible to use a single forward server, but for more demanding needs, it is suggested to have multiple machines to which you will have to manually divide the load; today, there is no balancing system that allows having a single FDQN or IP to reach.
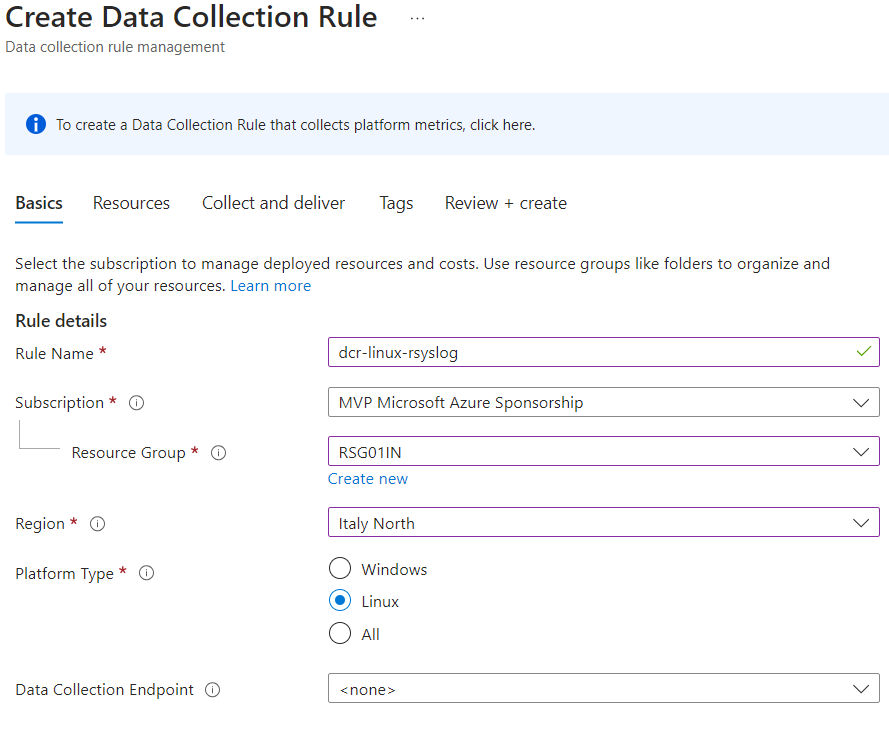
The advice is to create a DCR specifically for the forward log part to avoid mixing with other rules and needs in the Linux environment. After setting a name, using an appropriate naming convention, select the server you have just configured on Azure Arc.
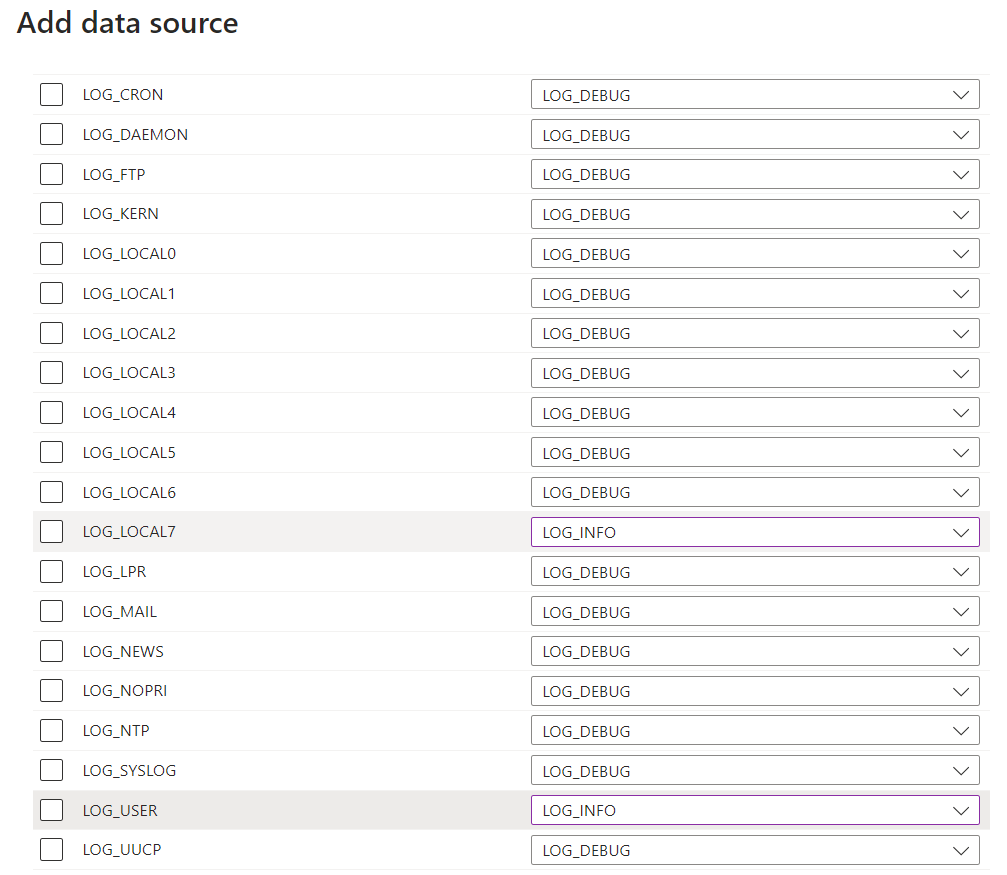
The DCR lists all the facilities recoverable in Linux: this field depends on how many devices you want to manage. The minimum level for collecting information must be set to LOGINFORMATION or LOGNOTIFY; all other attributes should be disabled to avoid generating unnecessary events but, above all, to contain the costs resulting from the continuous upload of data into Log Analytics.
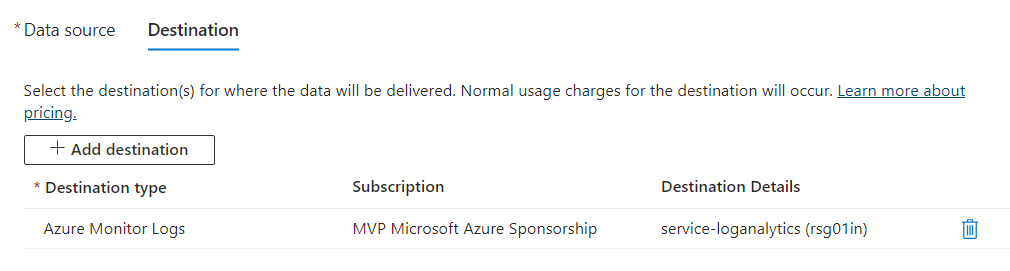
Once the Data Source part is completed, select the destination where to save the information – that is, the Log Analytics Workspace that you should have already created.
Another fundamental element for this scope is the activation of Microsoft Sentinel, Microsoft’s SIEM, which retrieves the information collected from Log Analytics to analyze and process it to notify dangerous or non-standard behaviors.
We will talk about Sentinel in more detail in another article, but for now, we focus on activating the Data Connector called Syslog via AMA, not to be confused with Syslog via Legacy Agent – the one that used MMA.
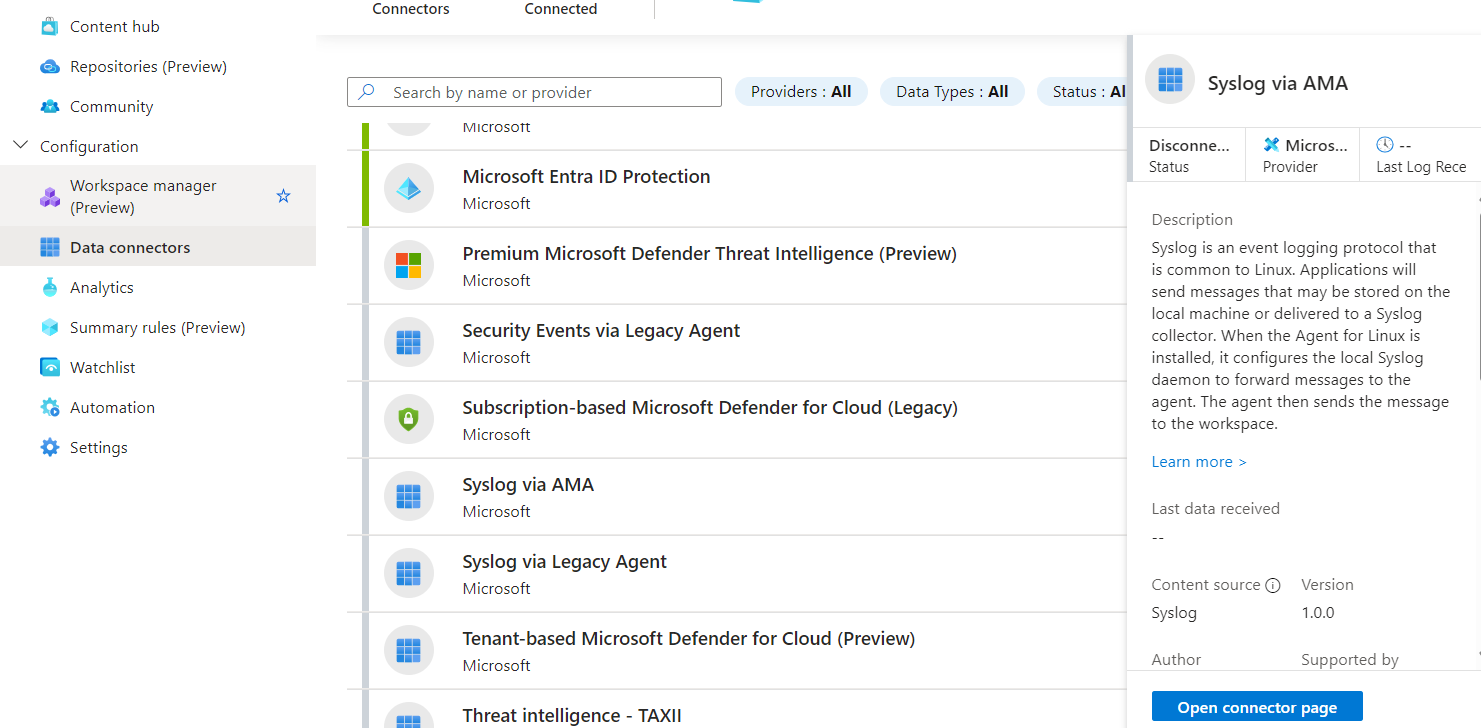
Within the configuration page, if you have correctly created the DCR, you will find the exposed rule and a command to launch inside the machine chosen to do rsyslog. This step is essential to allow the forwarding of logs from local to Log Analytics.
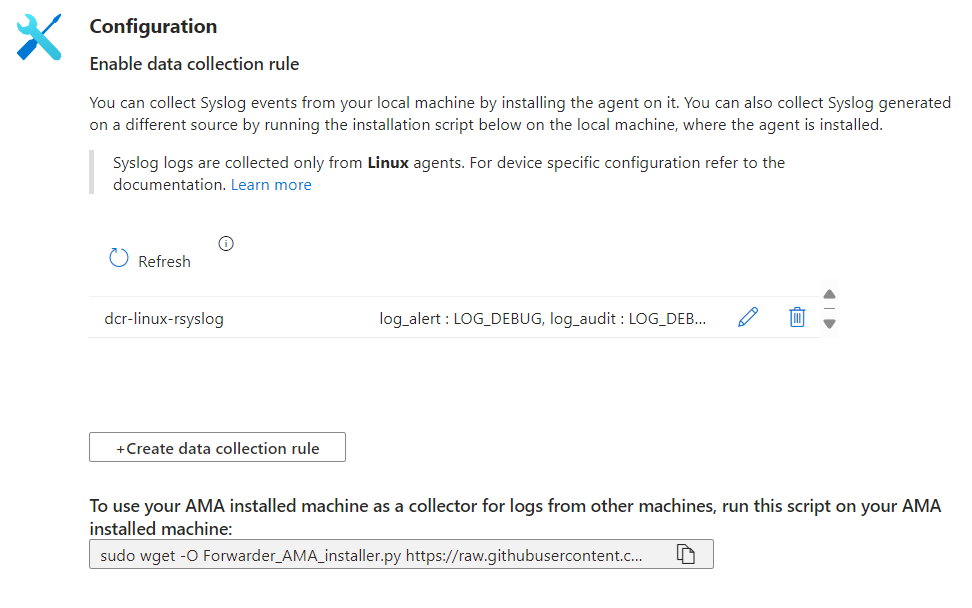
At the end of this operation, after about 10 minutes, and after setting Syslog as the destination for your devices, you can launch the Syslog query to see the result.
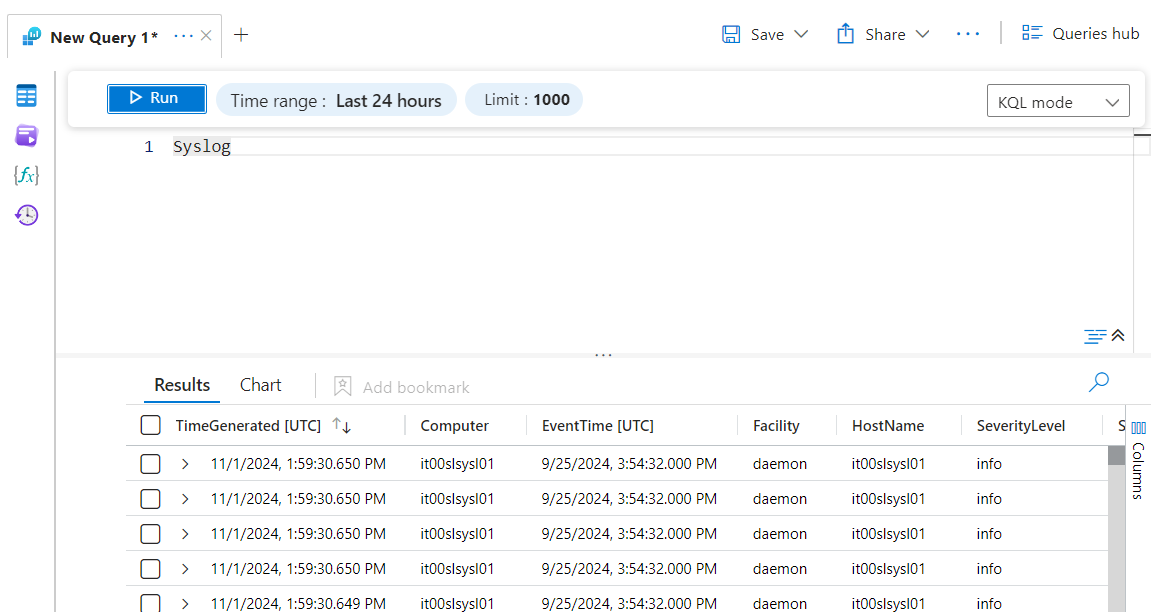
Finished! As for Veeam Backup & Replication, I refer you to this other article for the queries to know which facility to configure and which queries are usable – How to enable Veeam Backup & Replication logs with Azure Arc & Log Analytics.
Conclusions
Using a Linux machine configured as rsyslog allows moving another element of infrastructure management to the cloud. It is advisable to start with small tests and especially to correctly calibrate the type of logs moved from the device to the bridge to avoid both excessive and unnecessary ingestion of information and to contain the costs resulting from the increased capacity of Log Analytics.
#DBS