Questo articolo è disponibile anche in lingua italiana al seguente link: Windows LAPS: la gestione delle password si sposta in cloud – WindowServer.it
Microsoft Local Administrator Password Solution is a free product that has been around for a long time, but for some strange reason most IT admins only started to figure it out when they realized with using the same password for clients and servers, one was easily subjected to lateral attacks.
Microsoft LAPS is an agent that you install on each device you want to manage and that you drive via GPO allowing the following things:
- Change your password every X days
- Set a password complexity
- Change the local administrator account name
Credentials are saved within Active Directory and can be viewed from a specific client, subject to administrative delegation. It is immediately understood that LAPS increases security exponentially because each client/server has a different password, which should never actually be used to perform operations.
But LAPS is also excellent for full cloud scenarios, where there is no Active Directory structure, again due to the concept of lateral movement. All good, but in an era where full cloud scenarios are increasingly present, where multi-cloud environments are the order of the day and where PCs are increasingly outside the corporate perimeter, how do you increase security of client and server administrator account credentials?
Windows LAPS
Windows Local Administrator Password Solution is the evolution of this technology that sees five big news:
- Management through Microsoft Intune
- Saving credentials in Azure AD
- Viewing credentials from the Intune/Active Directory portal
- Credential rotation
- Password creation AD recovery mode
For the rest there have not been major changes compared to the past.
Windows Local Administrator Password Solution does not require special licenses, so you can also use it with the Azure Active Directory Free plan.
What versions of Windows are supported?
- Windows 11 version 21H2 and above
- Windows 10 version 20H2 and above
- Windows Server 2019
- Windows Server 2022
All these operating systems must be updated with the April 2023 patches, because Windows LAPS is now an integral part of the operating system and no longer needs to be installed separately, as was the case with Microsoft LAPS. It remains out of Windows Server 2016 which will still have to be managed with the old client mode.
So, if you have already deployed this solution you need to plan your migration activities well, using Legacy Emulation Mode – Get started with Windows LAPS in legacy Microsoft LAPS emulation mode | Microsoft Learn.
In this article we will see the implementation scenario within Azure Active Directory, through Microsoft Intune, while in a future article we will see the deployment within Active Directory.
Setup in Microsoft Intune
Why should I save the client/server local administrator credentials in Azure AD and not in Active Directory? For the reason described above, which is that devices are increasingly outside the corporate perimeter and therefore being able to manage this type of policy remotely helps to increase security; moreover, Windows LAPS allows you to change the password as soon as it is used and this scenario is truly remarkable when the need to deliver credentials directly to the end user is created.
Another scenario, closer to servers, is to want to change the password of a specific device when you suspect it has been compromised.
Before creating the policies within Intune, it is necessary to activate the LAPS functionality within the Azure AD tenant.
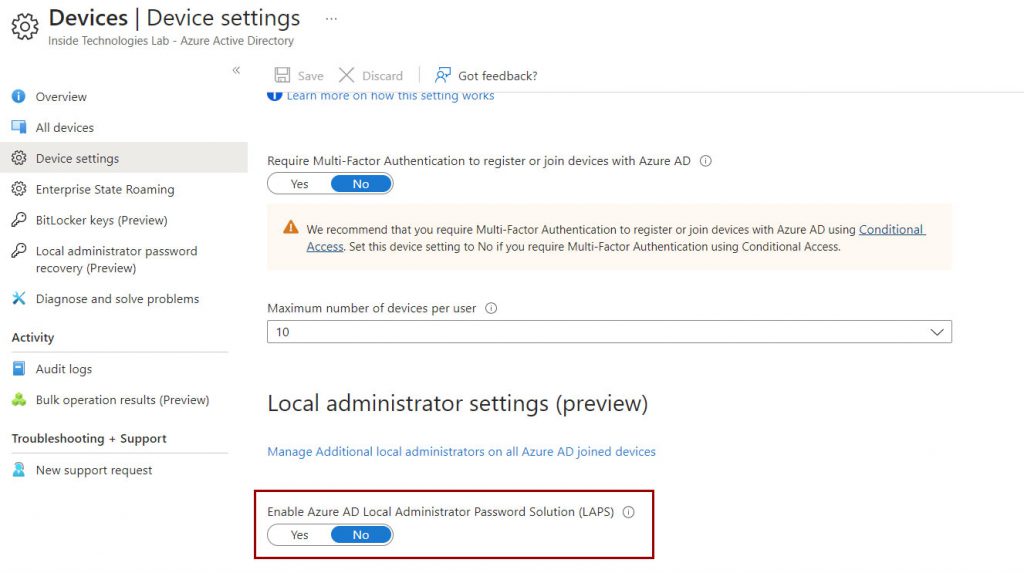
The second step is to create a new management policy, which can be found in the Endpoint Security -> Account Protection section.
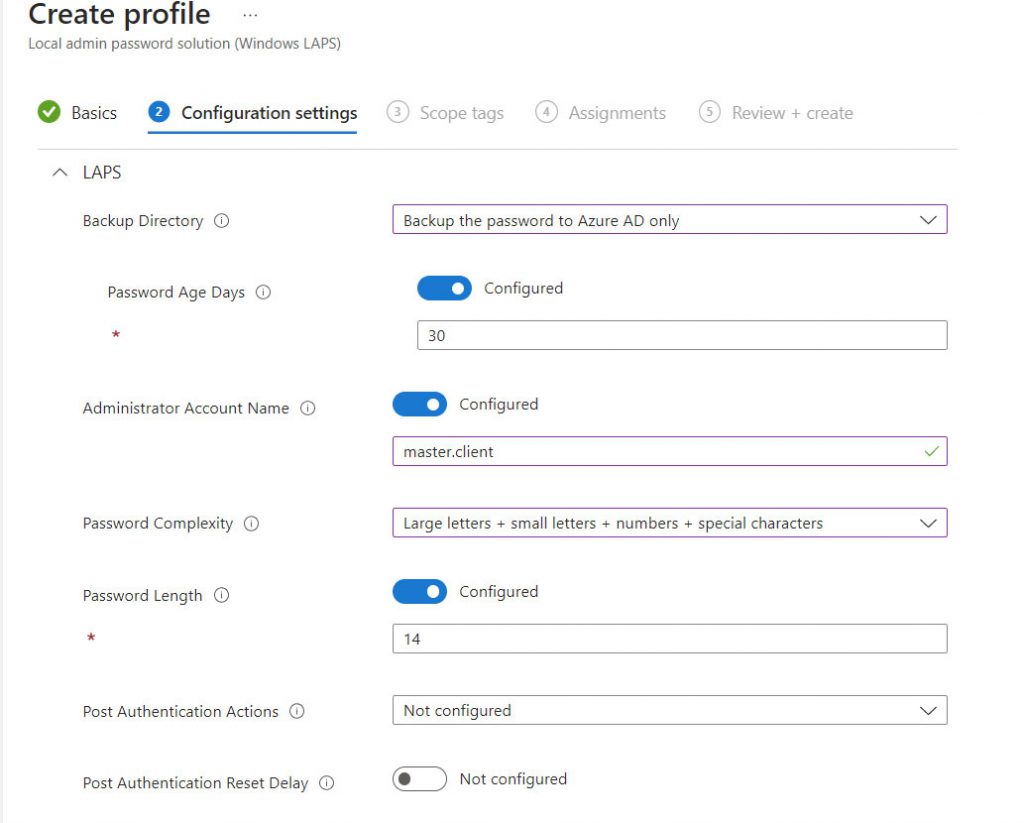
The fields are easy to understand but let’s try to analyze them:
- Backup Directory: where to save credentials (in this case Azure AD)
- Password Age: duration of the credentials
- Administrator Account Name: it is the name of the administrative user to manage (do not touch if you use the classic Administrator)
- Password Complexity: should I explain this?
- Password Length: as above!
- Post Authentication Actions: how the device should behave when the password is used
This last step is the one presented earlier and may have a note of interest, especially if you do not intend to use extra tools like Endpoint Privilege Management to allow your users to perform tasks with elevated privileges.
The policy must be distributed for all your devices, clients or servers, that you intend to manage.
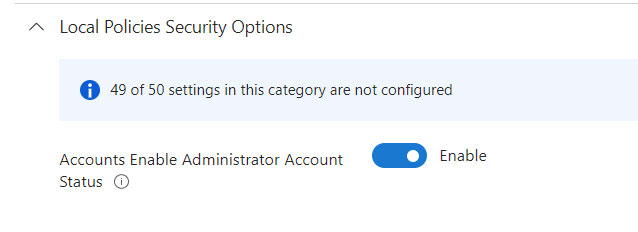
Finished? Practically yes, but an important step remains to be done: activate the local admin. This operation is mandatory for all full cloud clients, as the administrator user is deactivated by default, but the same dynamics could also occur in a domain environment.
Activation can be done with an Intune Configuration Policy, using the new Settings Catalog model.
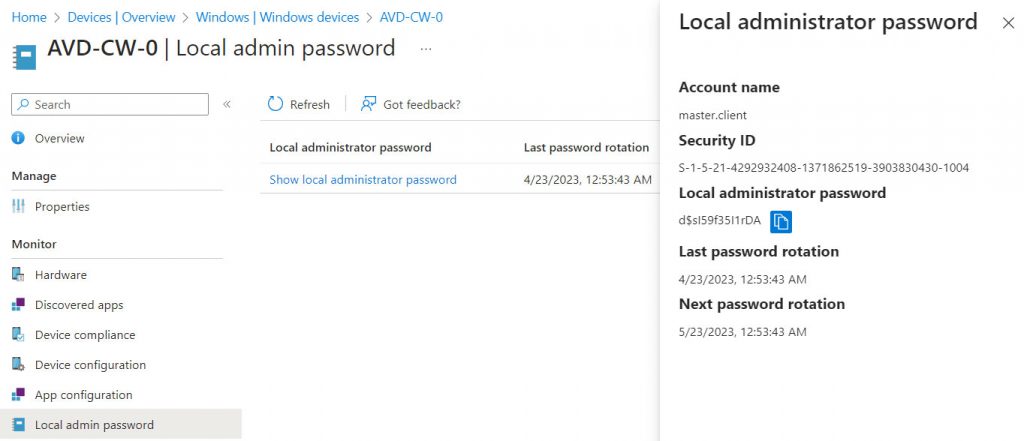
Credential Management
The password can be retrieved from the Microsoft Intune portal by clicking on the machine in question.
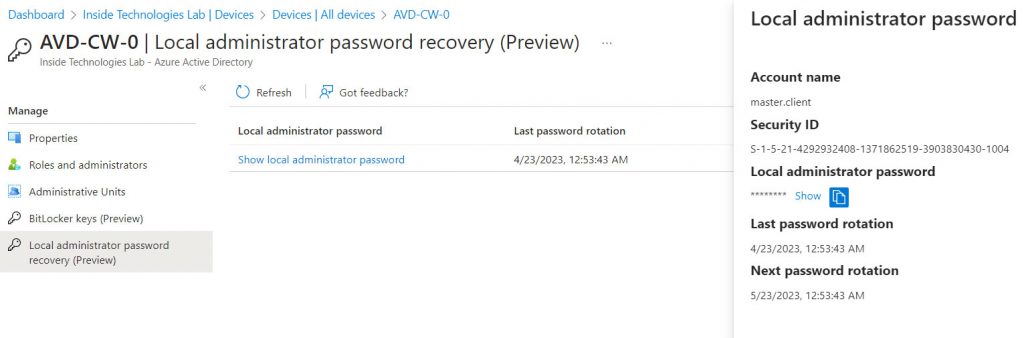
Or using the Azure AD portal if you don’t have Intune.
Password Rotation
The password, as seen, is renewed based on your policy but can also be updated upon request and to do so it is necessary to go through the Intune portal because the operation is not yet supported in Azure AD.
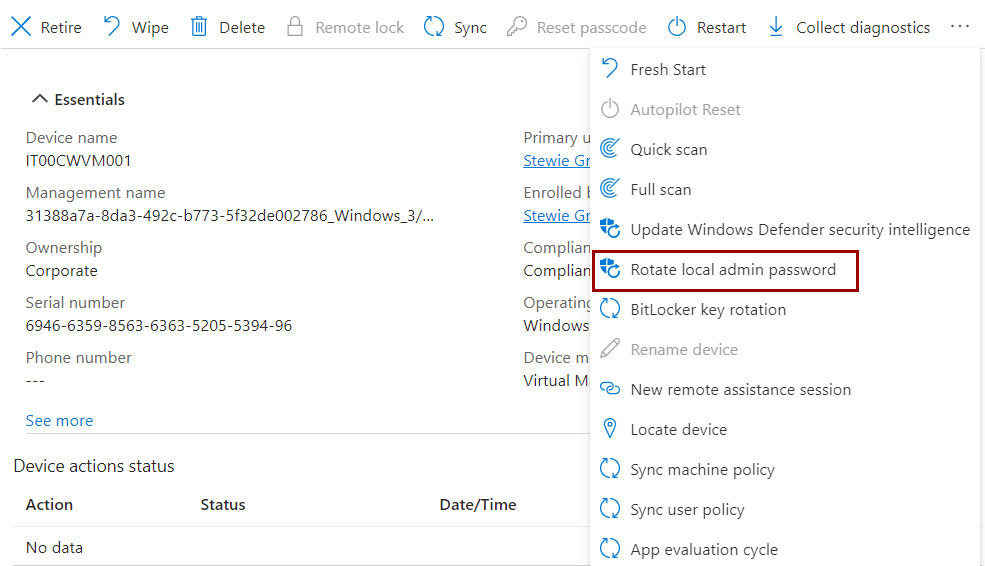
But who can rotate the password? Definitely the Intune administrator but also a delegated user – such as the helpdesk. To create a delegation, it is necessary to create a new Custom Role, selecting the Rotate Local Admin Password permission, and assigning the role to authorized users.
Event Viewer
How do you know that the password has been updated? There are logs about this that can be used to understand if everything is ok:
- 10003 – LAPS policy processing begins
- 10004 – LAPS policy processing success
- 10005 – LAPS policy processing failure
- 10018 – LAPS updated Active Directory
- 10029 – LAPS updated Azure Active Directory
- 10020 – LAPS updated local admin account
- 10031 – LAPS blocked external password modification request
- 10041 – LAPS detected successful authentication
- 10042 – Post-authentication grace period expired
- 10043 – LAPS failed to reset password
- 10044 – LAPS reset password & completed post-authentication actions
Having said that, the local admin credentials should never be used except in case of emergency and therefore you can do random checks on your clients to verify that everything is ok on the update side.
Conclusions
Endpoint Privilege Management is certainly a very powerful tool that allows you to offload the IT department by offering a perfect balance between control and security. For more information, you can refer to the official documentation at the following link – Configure policies to manage Endpoint Privilege Management with Microsoft Intune | Microsoft Learn.
#DBS