Questo articolo è disponibile anche in lingua italiana al seguente link: Microsoft Defender for Endpoint: prevenire Egregor Ransomware | WindowServer.it
The 2020 ended with the arrival of a new protagonist in the already vast panorama of ransomware, which has affected hundreds of companies, from SMB to Enterprise. Egregor, this is its name, combines techniques of the most devastating malware of recent years, combining techniques and strategies already used by numerous operators in the sector.
The main method of spreading this particular ransomware follows the classic malware distribution methodologies:
- Phishing
- Bad Links
- Vulnerability Attack
As with all ransomware, Egregor, once it enters the target systems, encrypts all the files it can hit, such as documents, databases, backups, etc. In this case, the extension that is assigned by Egregor is randomic, which makes it difficult to block, together with the XOR marker.
Attack Schema
What is striking about the attack system is the escalation with which the ransomware acts. Once the client is taken over, the credentials are stolen from the Windows Credentials Manager, analyzing all available accounts, trying to immediately disable antivirus, backup systems and everything that would allow the user to be able to restore.
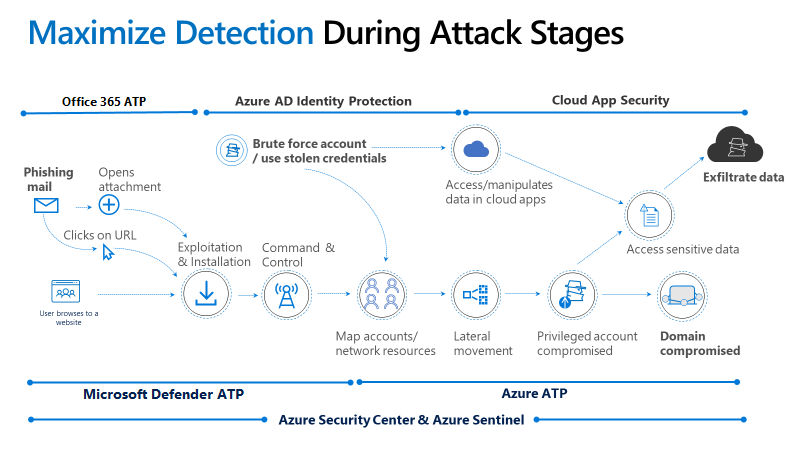
But Egregor’s “cunning” does not stop there, because with the same credentials an escalation to other clients and servers is initiated. The final result is the total encryption of the entire company, the loss of backups and damage caused by the downtime.
Regarding the encryption algorithms used, Egregor combines AES (Advanced Encryption Standard) with RSA-2048 and ChaCha. AES is the preferred encryption algorithm of governments, financial institutions and businesses, and this make impossible to decrypt.
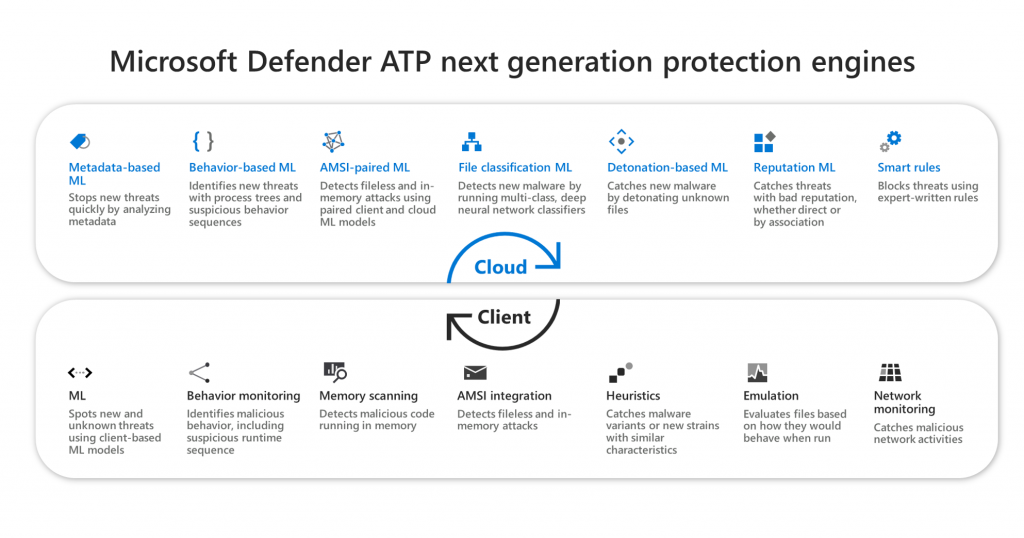
Microsoft Defender for Endpoint
Microsoft Defender for Endpoint is the perfect solution to defend your devices, clients/ smartphones, and servers from attacks like these through a Machine Learning system that allows you to act immediately in case of suspected corruption of the machine (such as automatic isolation from network).
Prevent Egregor
To prevent the attacks generated by Egregor it is necessary that Defender is powered to know what it has to stop, in the form of hashes, IP addresses or domains. This thing is manageable within the Settings – Indicators section
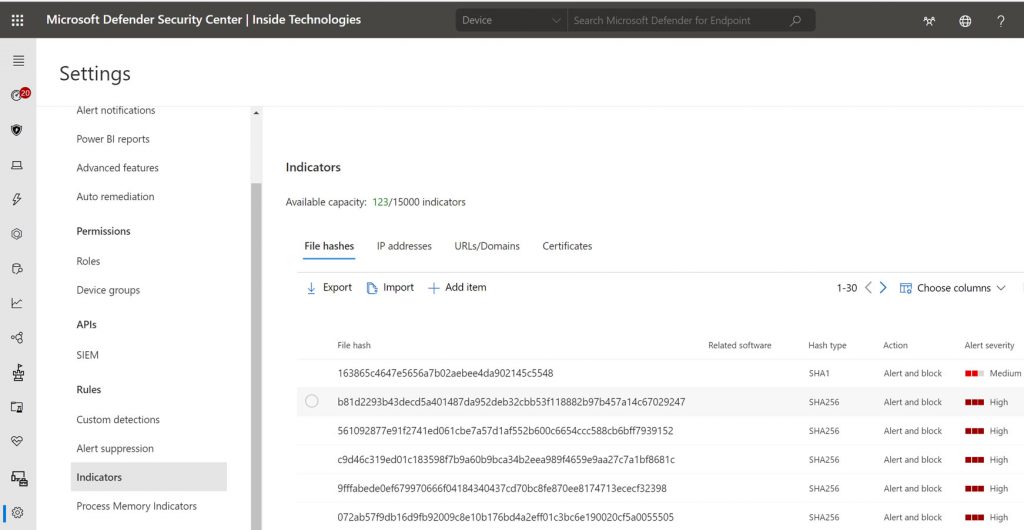
The list of indicators linked to Egregor is available at the following link: InsideTechnologiesSrl/MSDefenderATP (github.com)
Conclusions
We must never let our guard down against this type of attack and it is for this reason that it is essential to have the right tools to reduce the risks of business downtime that could cause enormous economic damage. From this point of view, Microsoft Defender for Endpoint is the best choice, thanks to the native integration with Windows 10 and Windows Server.
Get Started
Microsoft Defender for Endpoint
#DBS