Questo articolo è disponibile anche in lingua italiana al seguente link: Microsoft Defender for Identity: implementazione e gestione | WindowServer.it
The protection of your IT infrastructure must pass strictly by the Domain Controllers, because they are the ones who authenticate the various objects but also because they are the first to be under attack by ransomware and malicious software.
A normal antivirus only serves to prevent certain activities but the Identity component requires something more targeted and capable of doing targeted analysis.
Microsoft Defender for Identity (formerly Azure Advanced Threat Protection, also known as Azure ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Setup
Microsoft Defender for Identity requires an Enterprise Mobility + Security 5 (EMS E5) license, but you can also get started by activating the trial.
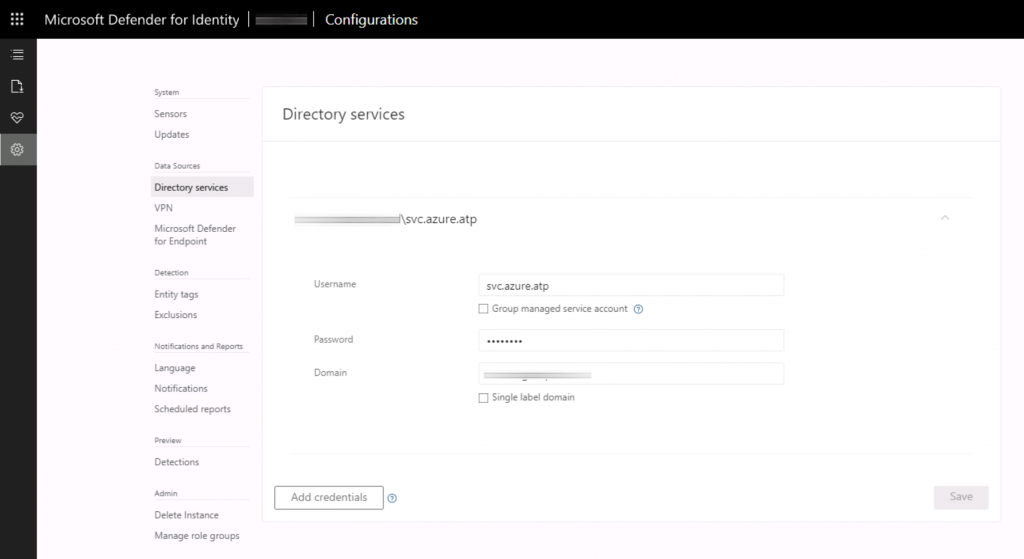
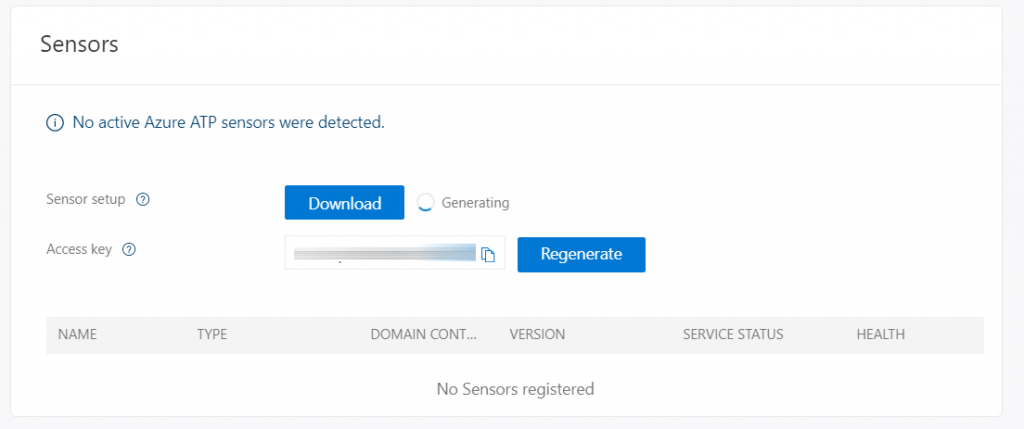
The first step is to set up an account capable of scanning the Active Directory infrastructure; this account must not have any particular privileges. Subsequently it will be possible to download the agent that must be installed on the various Domain Controllers; it will also be necessary to copy the Access Key used to create the link between the cloud subscription and the various objects – figure 2.
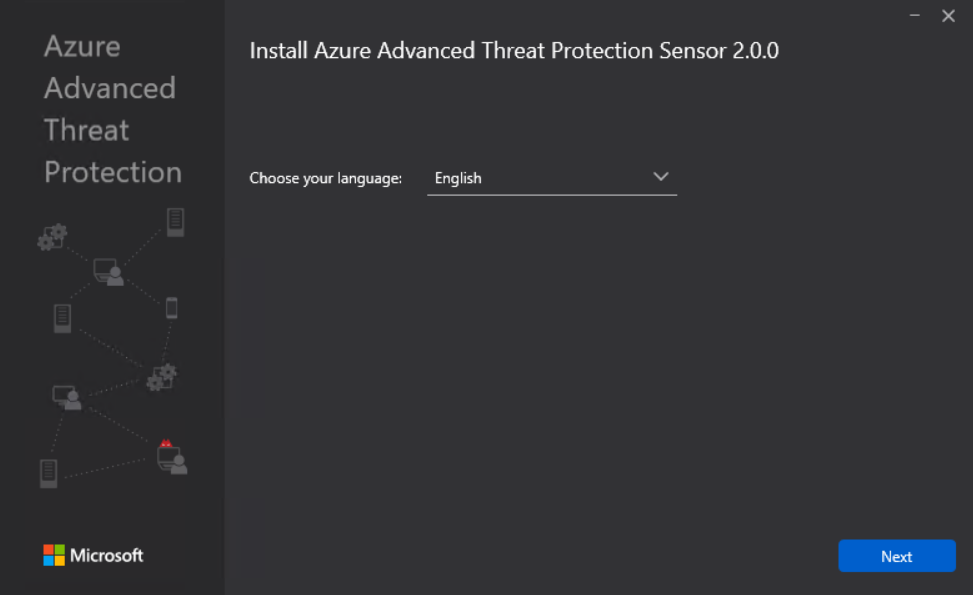
The installation is quite simple and requires only the insertion of the previously copied Access Key.
Analysis and Protection
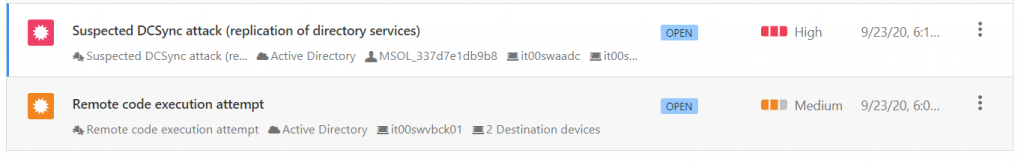
Once the scan has started, the first warnings will begin to arrive on the activities considered suspicious which obviously can be analyzed by drilling down on individual objects – figures 4 and 5.
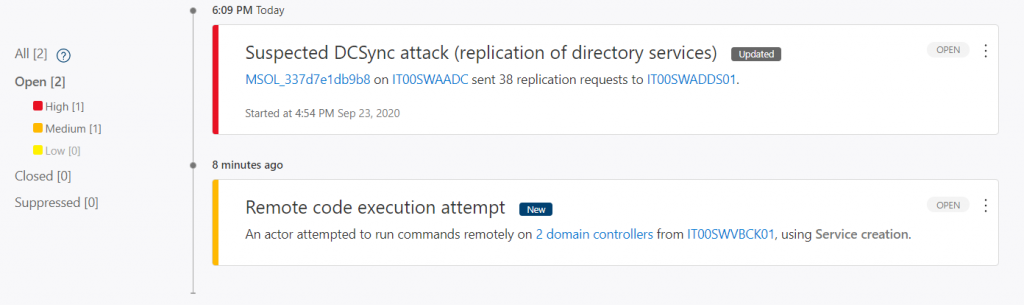
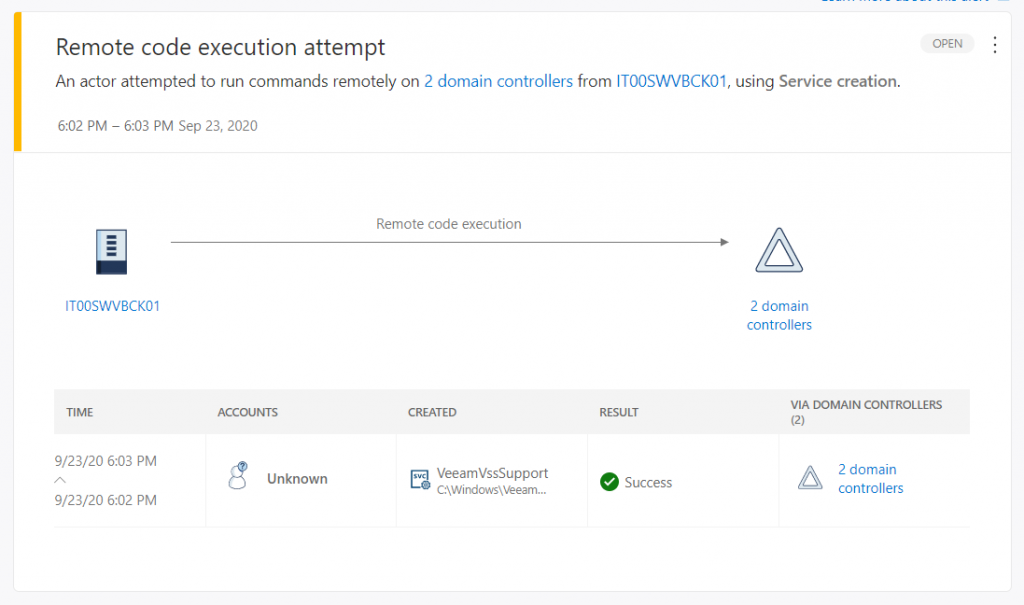
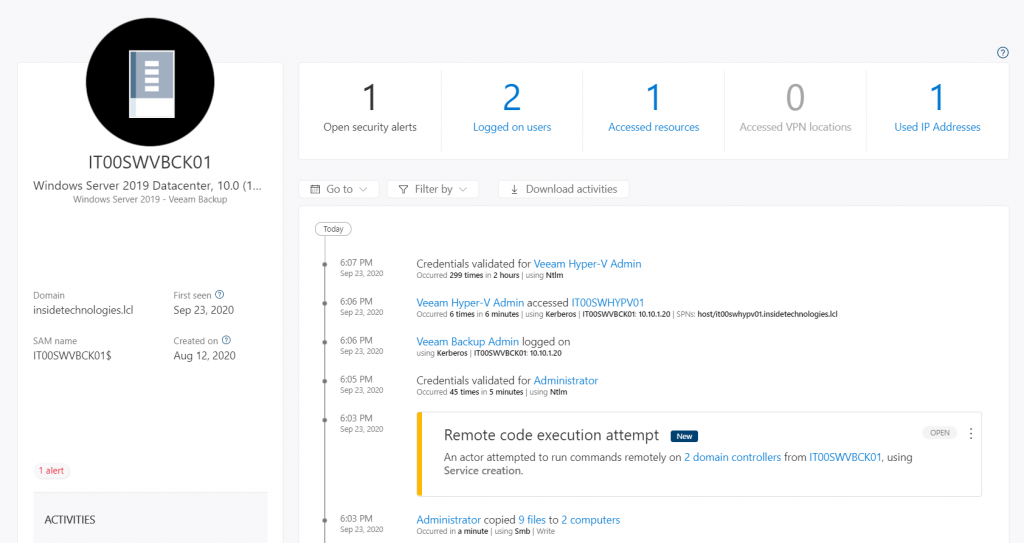
Defender for Identity monitors and analyzes user activities and information across your network, such as permissions and group membership, creating a behavioral baseline for each user. Defender for Identity then identifies anomalies with adaptive built-in intelligence, giving you insights into suspicious activities and events, revealing the advanced threats, compromised users, and insider threats facing your organization -figure 6.
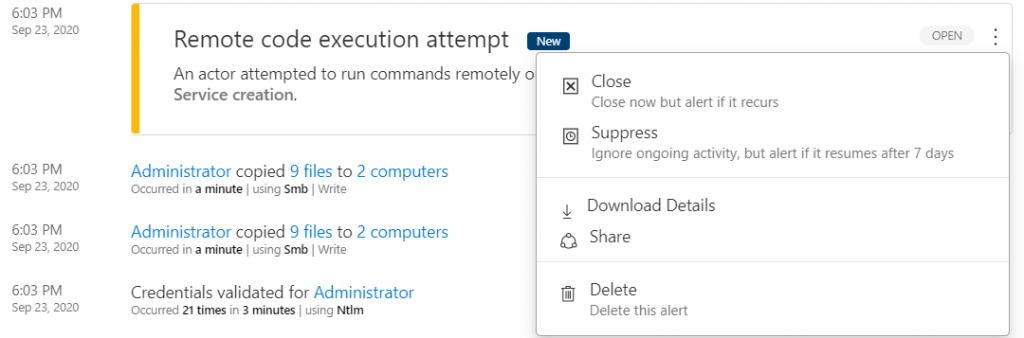
It’s important understand that Microsoft Defender for Identity does not immediately know what is right or what is wrong, so it is essential to fine-tune the processes and accounts that are deemed correct – figure 7.
Integration with Cloud App Security
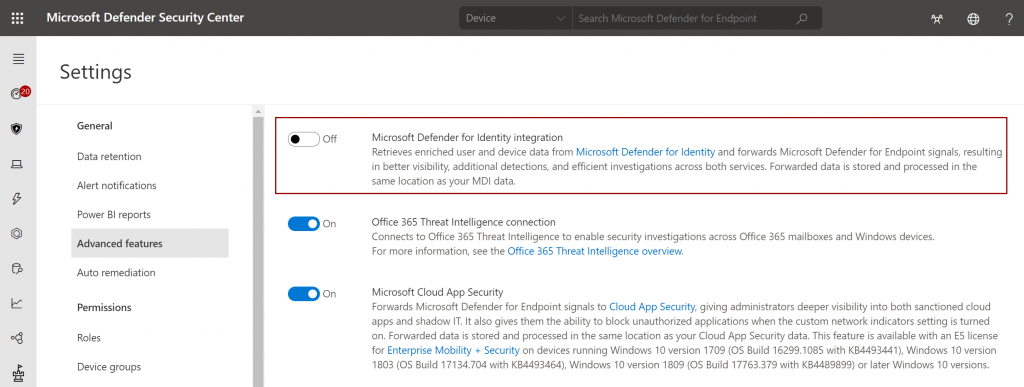
The Microsoft Defender for Identity console is being phased out to allow for greater integration with Cloud App Security and Microsoft Defender for Endpoint.
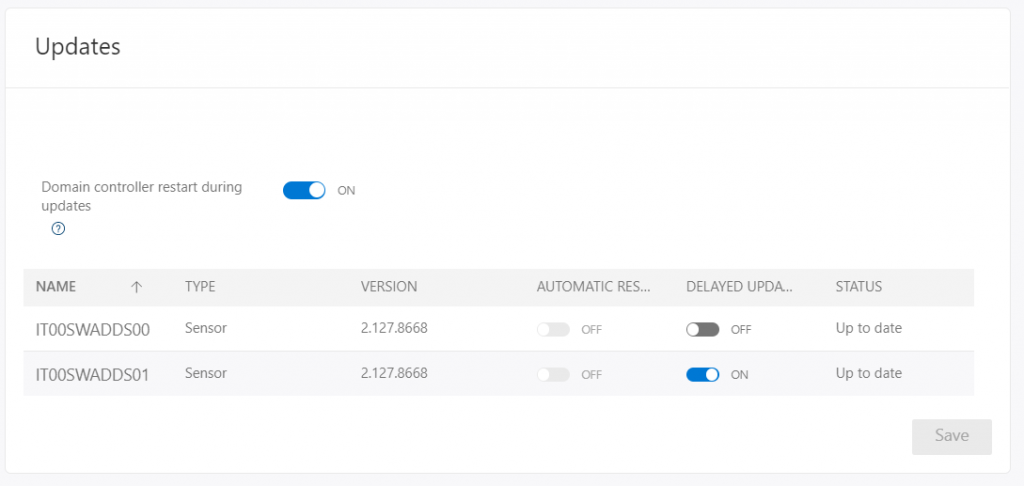
Agent Update
The agent update can be done manually or automatically, however in the second case it is possible that the servers are restarted and this could create disruptions. For this reason it may be useful to set the delay in restarting the machines, so as to always leave a Domain Controller active.
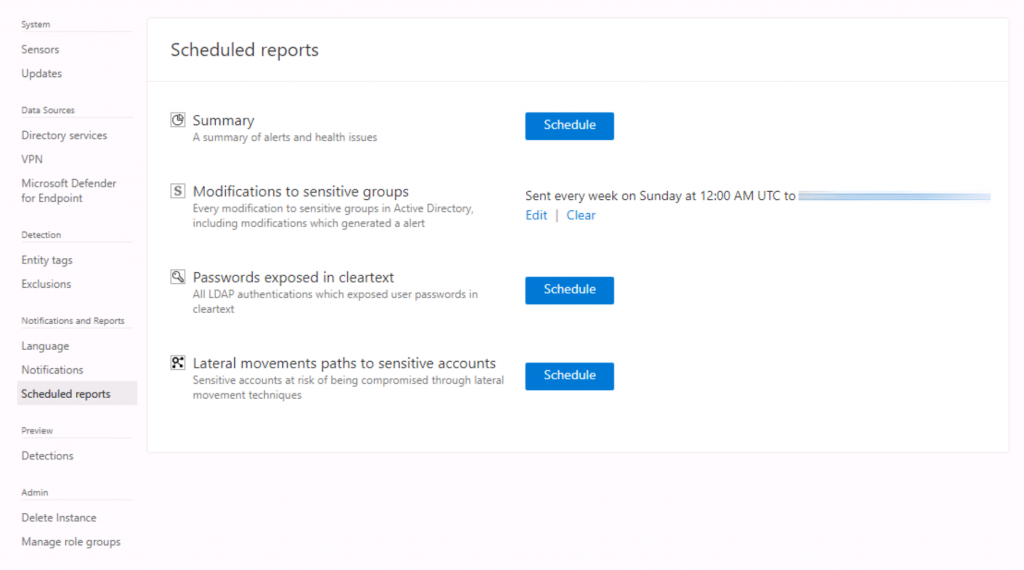
Reporting
Microsoft Defender for Identity reporting allows you to notify administrators about various suspicious activities such as changing system groups. Through security reports and user profile analysis, Defender for Identity drastically reduces the organization’s attack surface, making it more difficult to breach user credentials and carry out an attack.
Conclusions
Microsoft Defender for Identity is the perfect solution for protecting your Active Directory infrastructure capable of identifying, detecting and analyzing advanced threats. Thanks to the integration with Machine Learning logic, it is possible to prevent the corruption of your Domain Controllers quickly and automatically.
Get Started
Enable Microsoft Defender for Identity
#DBS