Patching is critical to keep safe your IT infrastructure but sometimes is complex, in particular when you have many servers based on a different OS vendors and deployed in many places like on-premises, Azure, AWS, GCP.
Create an maintenance plan is good way to avoid security issues. With Microsoft Azure this was possible thanks to Azure Automation, a solution that give you the possibility to create updates schedule plan for Windows and Linux. You can find more details in this my article – Microsoft Azure: implement Update Management.
The requirement to manage multi-machines in multi-environment push Microsoft to change the logic behind Update Management and this is the goal of the v2.
Benefits
There are many benefits around this new release, like
| Central visibility for updates | Native experience with zero onboarding | Works with Azure roles and identity | Enhanced flexibility |
| – Oversee update compliance for entire fleet of Windows and Linux machines including Azure machines and Azure Arc-enabled servers on a single dashboard. – View compliance status for each individual machine, easily deploy updates, and track results. | – Built as native functionality on Azure Compute and Azure Arc for Servers platform for ease of use – No dependency on Log Analytics and Azure Automation – Azure policy support – Scale to the limits of ARM and resource RP – Global availability in all Azure Compute and Azure Arc regions | – Granular access control at per resource level instead of access control at Automation account and Log Analytics workspace level – Update management center now as Azure Resource Manager based operations. It allows RBAC and roles based of ARM in Azure | – Install updates right away or schedule them for a later date – Check updates automatically or on demand – Secure machines with new ways of patching such as Automatic VM guest patching in Azure, Hotpatch, or custom maintenance schedules – Use periodic assessment and scheduled patching at scale with Azure Policy – Sync patch cycles in relation to Patch Tuesday—unofficial term for Microsoft’s scheduled security fix release on every second Tuesday |
So, from my point of view the most important point is “No dependency on Log Analytics and Azure Automation” because Update Management v2 is based on Azure Arc, much lighter and more scalable compared the old Log Analytics agent (aka MMA).
Configuration
To use Update Management v2 is request install Azure Arc agent inside your servers. If you don’t know what is it, check this link: Azure Arc – Gestione di soluzioni ibride e multi-cloud | Microsoft Azure.
Is not complicated configure a patch plan but before of this, is necessary configure the Periodic Assessment: this is a way to understand the update status of your servers. The scan can be set manually for from Azure Policy.
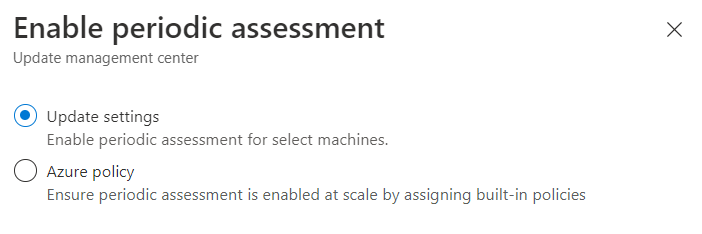
The choice is based on the complexity of your infrastructure because if you have always the same 20 VMs, the manual set is ok; but if you have several machines around the multi-cloud, with high-rotation, the Azure Policy is mandatory.
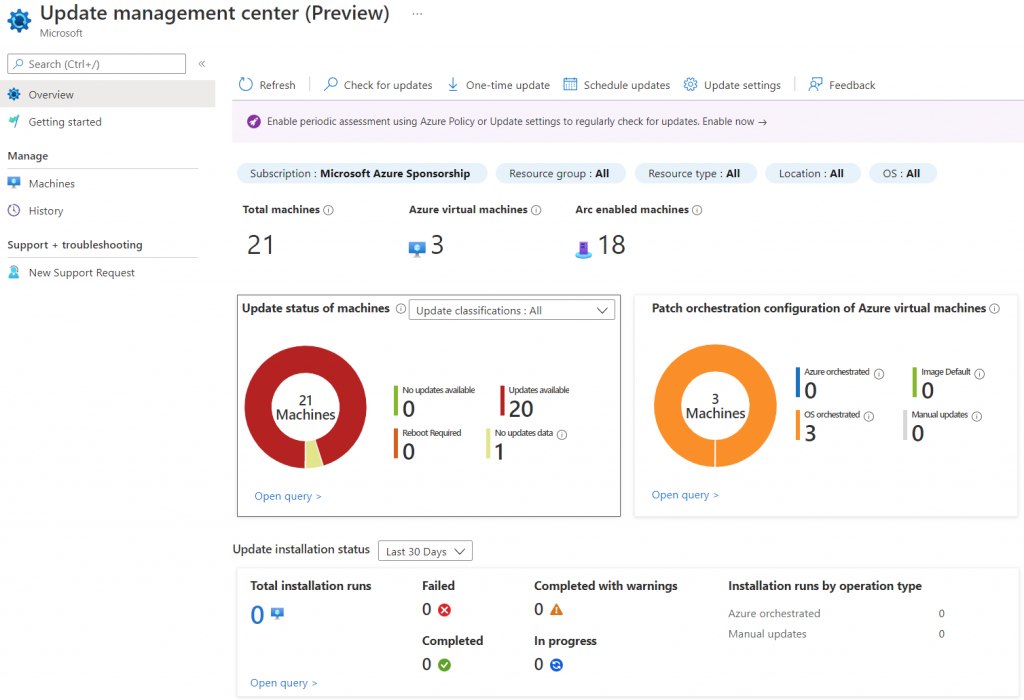
After the first scan, you have the full status of servers.
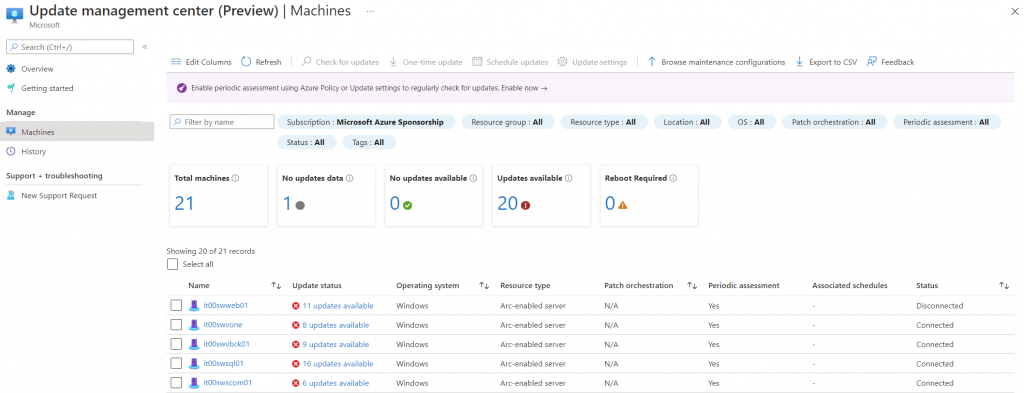
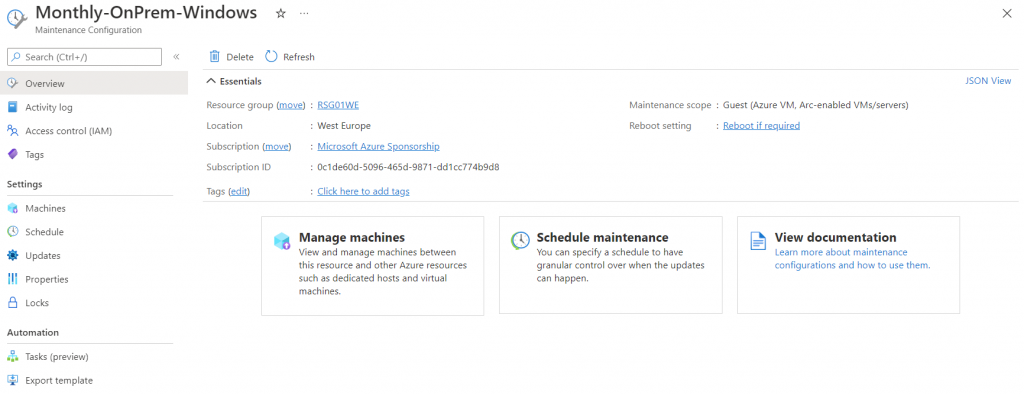
To create a new maintenance plan, select the servers you want include and click on button Browse Maintenance Configurations.
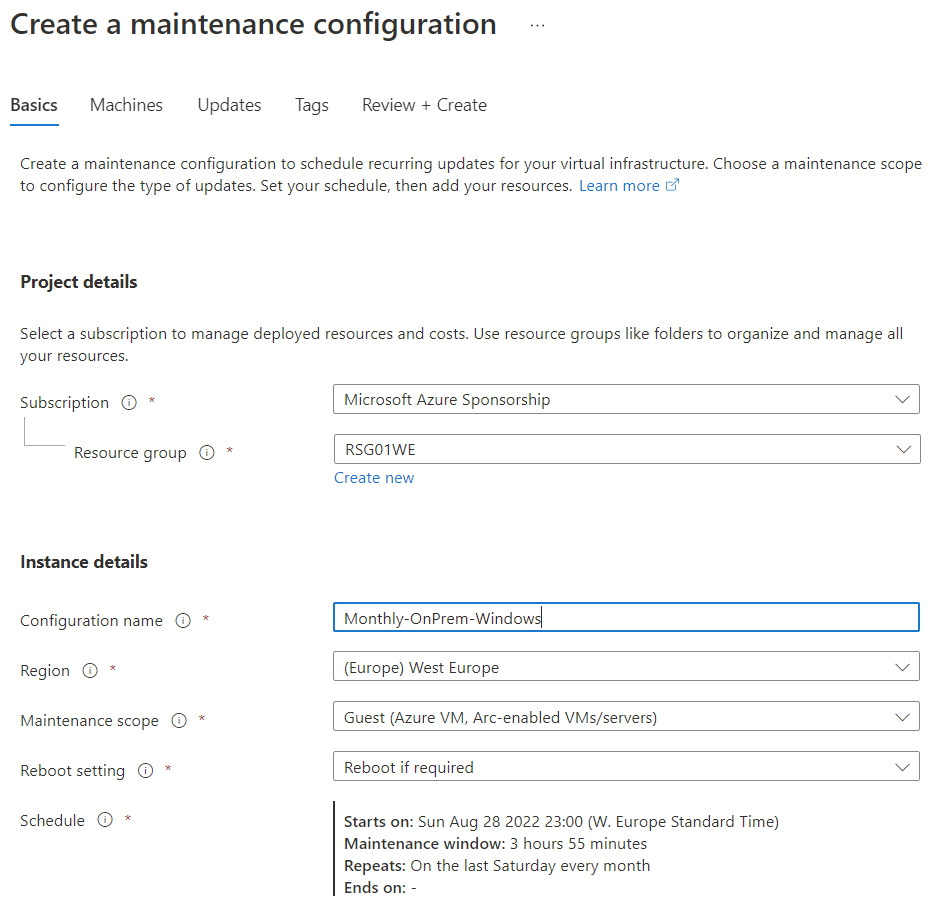
The plan is an ARM object and this means that can be managed via API or PowerShell or CLI.
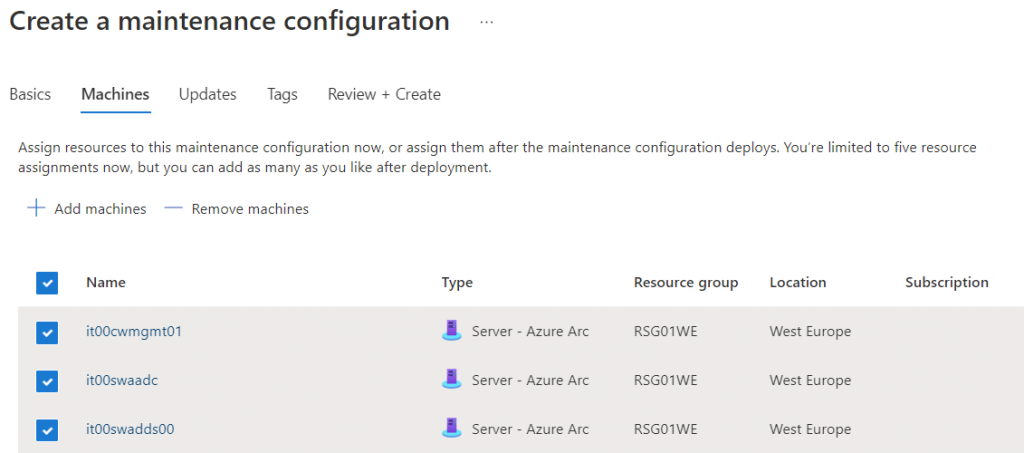
Add the machines into the plan. The next step is select what kind of updates install; like the old version, is possible include/exclude specific KB (for example if you want block a specific KB that can generate issue).
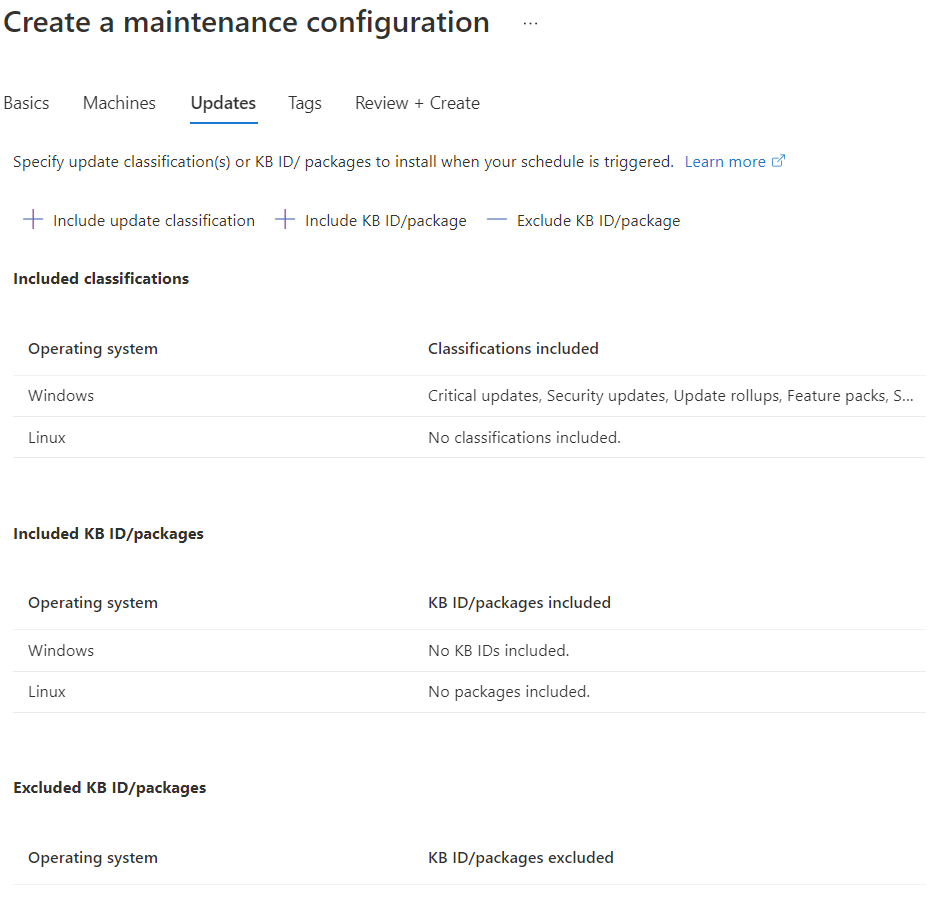
Done! If you want edit the rule, to change schedule, add/remove machines, change updates, you just recall the resource from Azure or from Update Management.
One-Shot Update
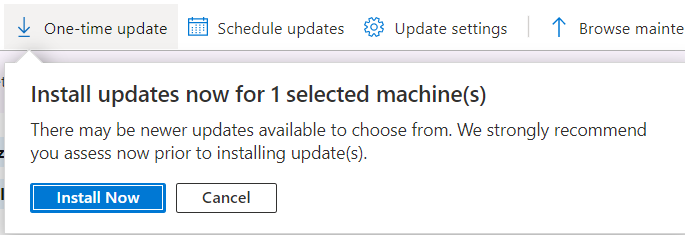
The difference with the past is the possibility to create a one-shot task to install updates to a single/multi machine.
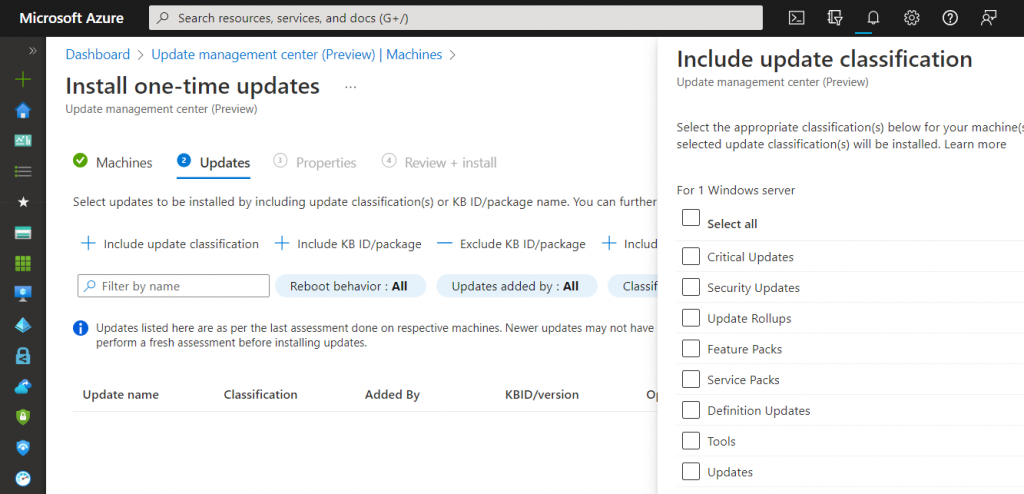
In this case you must select what kind of category include…
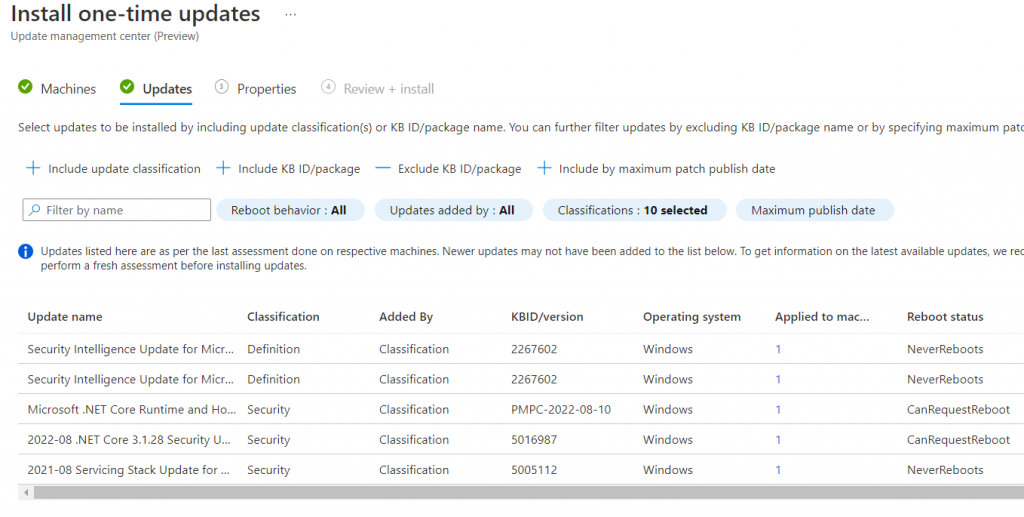
…to see what are the missing updates.
History
The history of your updates are available inside the dedicated view; you can drill-down to check the details.
Conclusions
Update Management v2 is absolutely a great solution to patch your servers, no matter if are Windows or Linux, on-premises or on Azure or AWS. The full integration with Azure Policy gives you the possibility to standardize the security posture.
Get Started
If you are interested to test the solution, this is your starting point: Update management center (preview) overview | Microsoft Docs
#DBS