Protect a virtual machine from attack is not easy, specially when it is exposed to external. The VMs on Microsoft Azure, like the others outside from internal infrastructure, requires more attention because we need to keep opened a channel to manage them so protocol like RDP or SSH must be available for the entire world.
Obviously, we can increase protection with simple tasks like add our public IP into the Network Security Group, to avoid connections different from this/these IPs, or we can create a VPN Point-to-Site from our client to Azure Network.
Today we can achieve the same result thanks to a new tool called Azure Bastion.
What is Bastion?
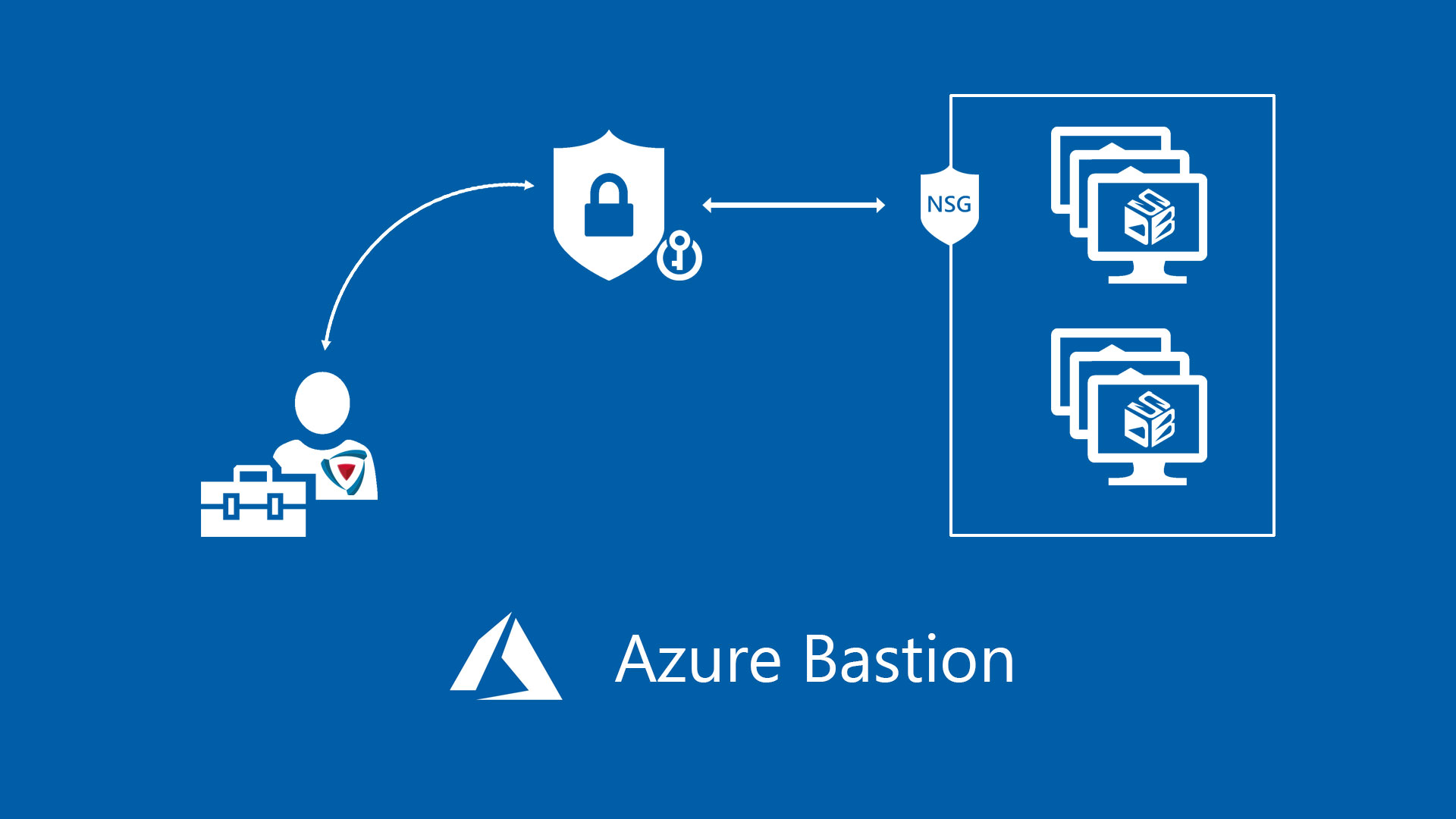
Azure Bastion is a new managed PaaS service that provides seamless RDP and SSH connectivity to your virtual machines over the Secure Sockets Layer (SSL). This is completed without any exposure of the public IPs on your virtual machines.
Behind the scenes there’s a dedicated Network Subnet on your Azure Network, that provided a gateway connection via HTML5 to your virtual machine. No more RDP or SSH protocols exposed and this can avoid also usage of public IP address.
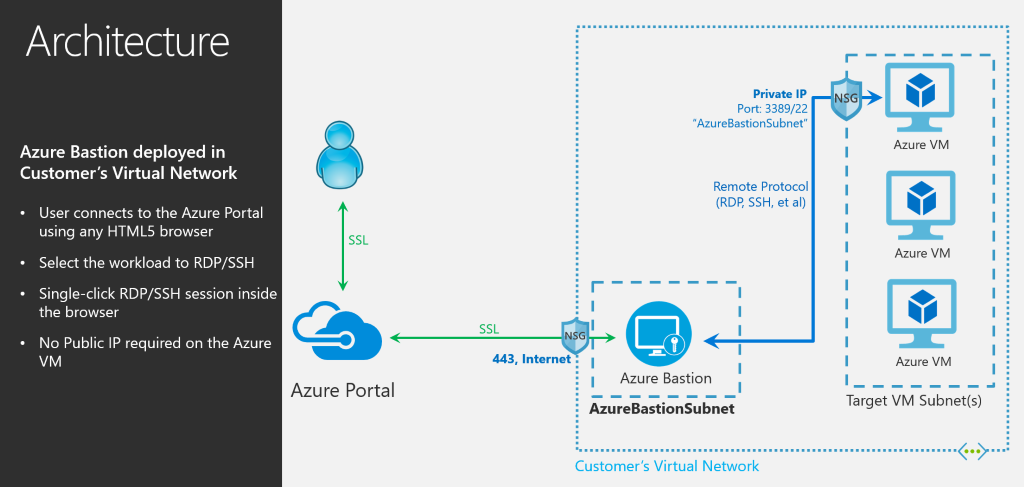
If you are asking why I should use Azure Bastion, bear in mind that this service helps the infrastructure to be more secure against port scanning, because you don’t need to expose RDP or SSH, and, very important, reduce the risks based on zero-day exploits on these protocols; this is fundamental to protect information and integrity of our servers. Last but not least, it works with Windows and Linux!
The preview has these key features available:
- RDP and SSH from the Azure portal
- Remote session over SSL and firewall traversal for RDP/SSH
- No public IP required on Azure Virtual Machines
- Simplified secure rules management
- Increased protection against port scanning
- Hardening in one place to protect against zero-day exploits
Deploy Azure Bastion
Before starts with deployment, remember that the public preview is provided without a service level agreement and should not be used for production workloads. The service is available only in few Regions so check the documentation before.
From your Azure subscription, open a Cloud Shell session in PowerShell mode. If you are not familiar with the tool, check my article to configure it.
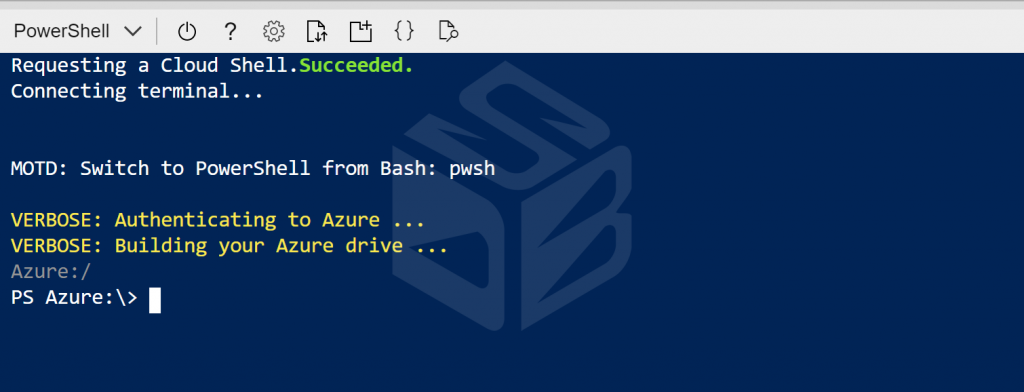
Run these commands:
Register-AzureRmProviderFeature -FeatureName AllowBastionHost -ProviderNamespace Microsoft.Network
Register-AzureRmResourceProvider -ProviderNamespace Microsoft.Network
Get-AzureRmProviderFeature -ProviderNamespace Microsoft.Network
After few minutes the service will be available on your tenant.
To use this preview, is necessary open a dedicated link – http://aka.ms/BastionHost – the result will be like the figure 3 (with a orange top bar instead your classic color).
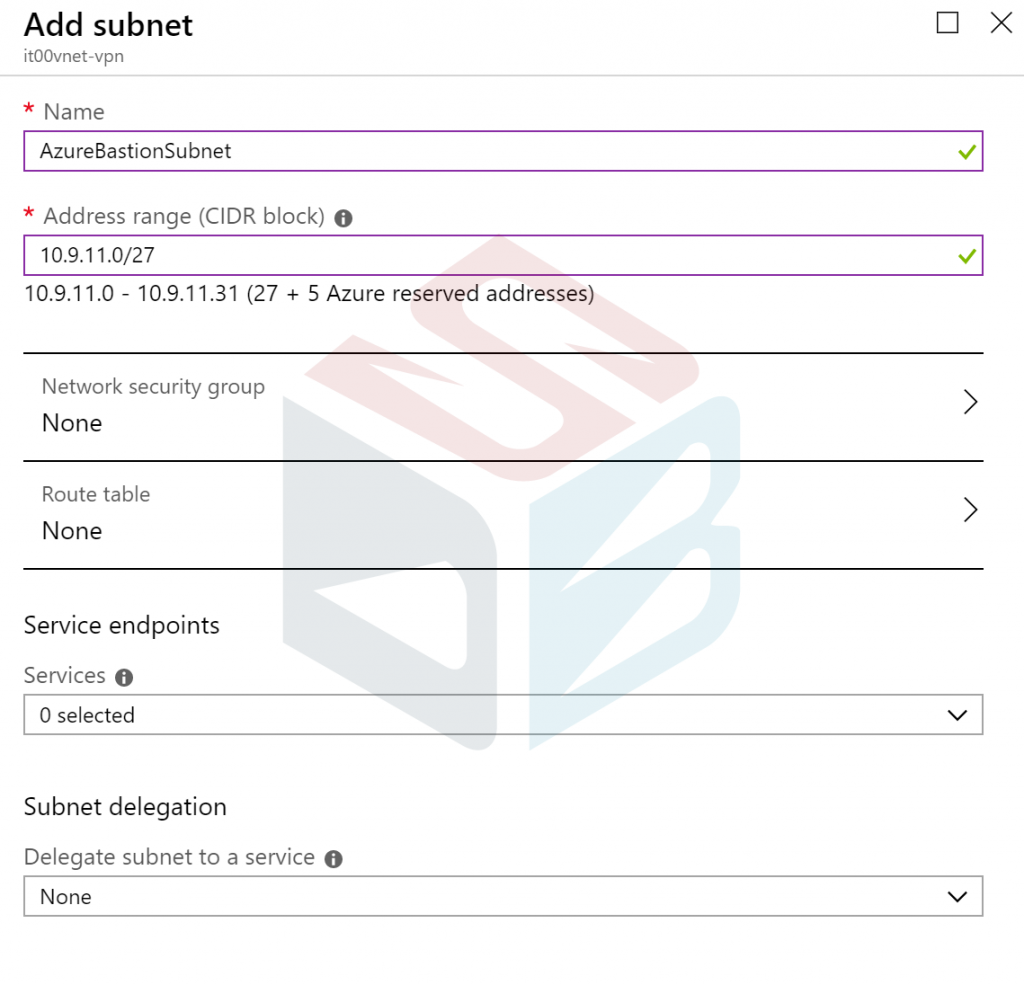
Before to create Bastion service, is required add a new Subnet into the network that you want manage through this service; the name of subnet must be AzureBastionSubnet and it’s important don’t configure NSG, delegation or route table and the address range should be /26 or /27.
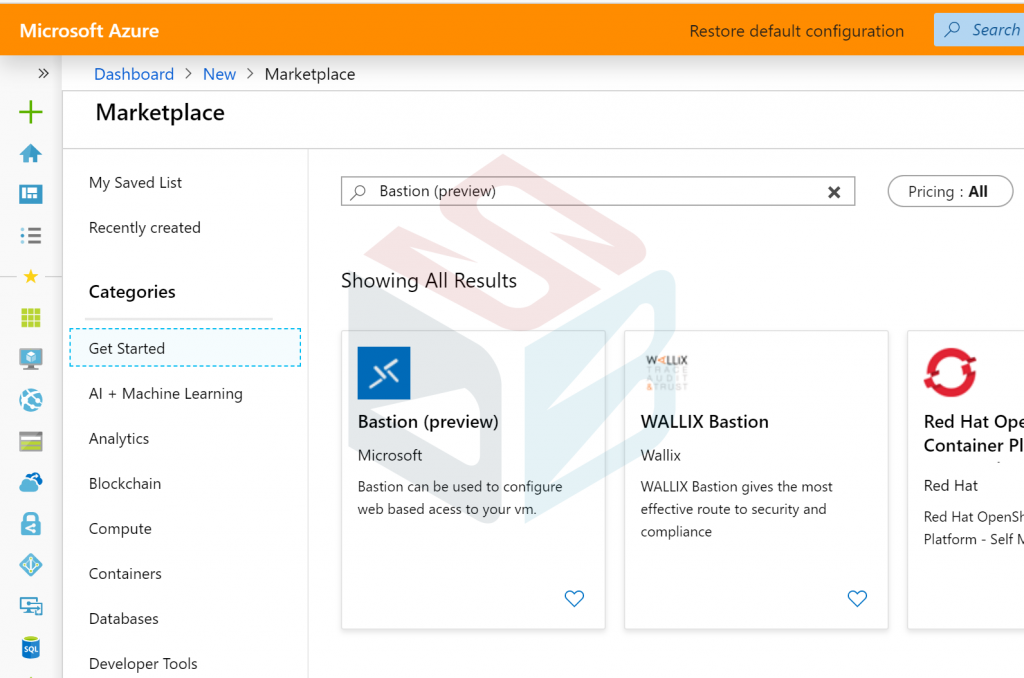
Now we are able to create a new resource from Marketplace – search Bastion (Preview) – figure 5.
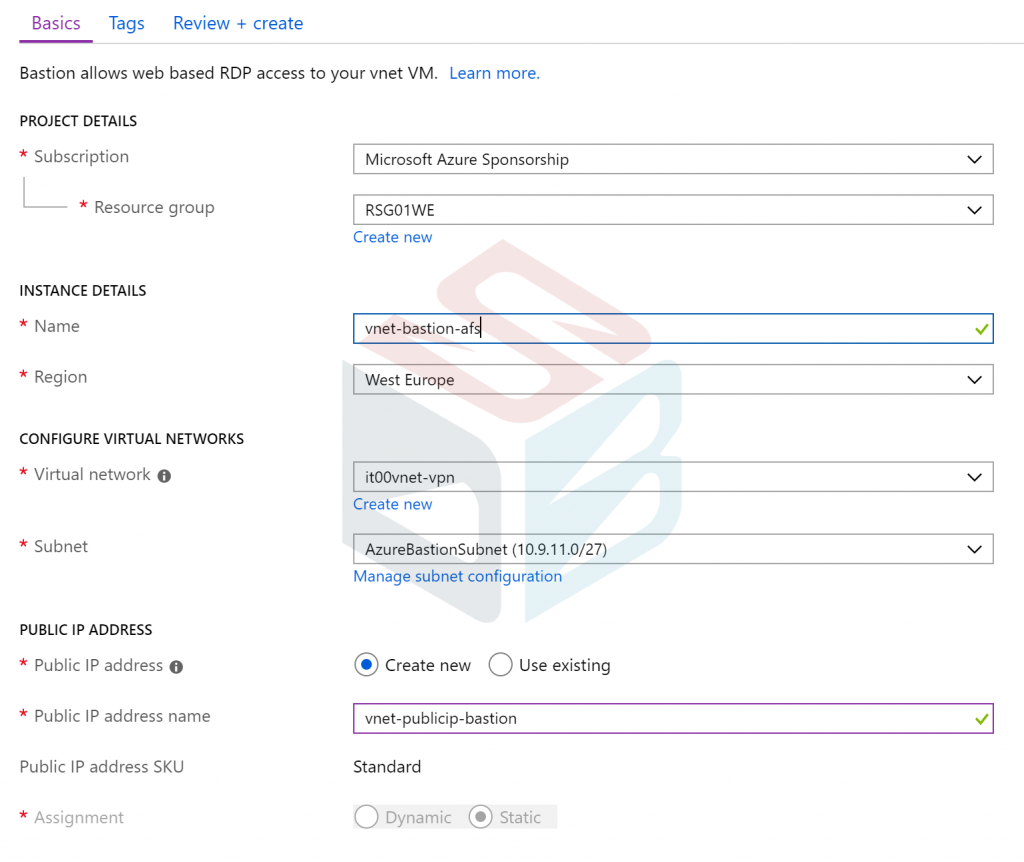
The wizard is very simple and requires some values to configure the service.
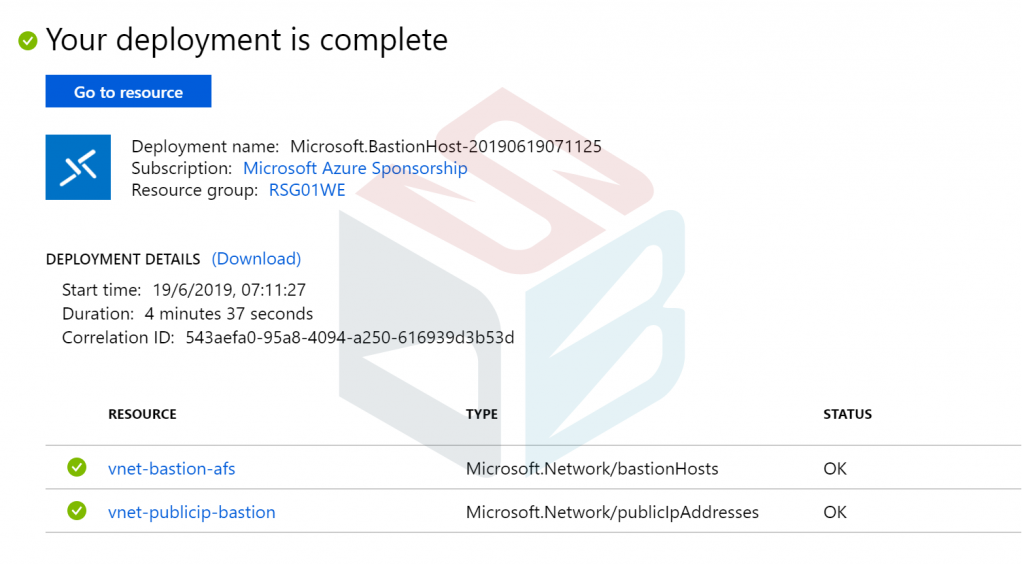
Once the object will be created, the portal shows you the end of work.
To use Bastion, click on your Azure virtual machine, select Connect and choose Bastion as modality. Insert username and password of your domain/local account to establish connection.
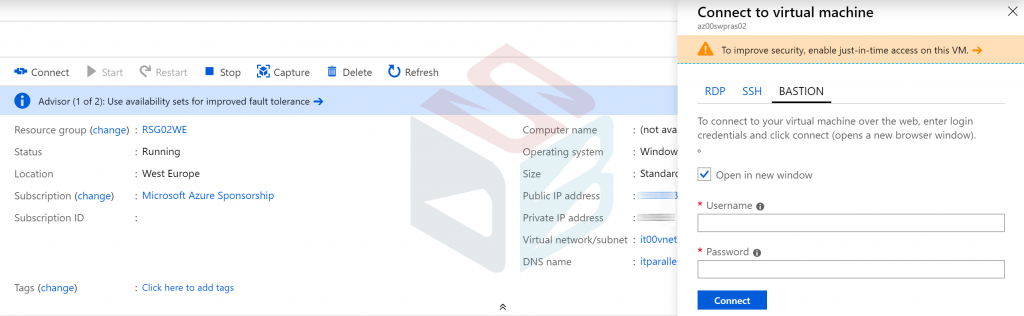
Note: don’t forget to use the Preview portal and to enable the popup on your browser.
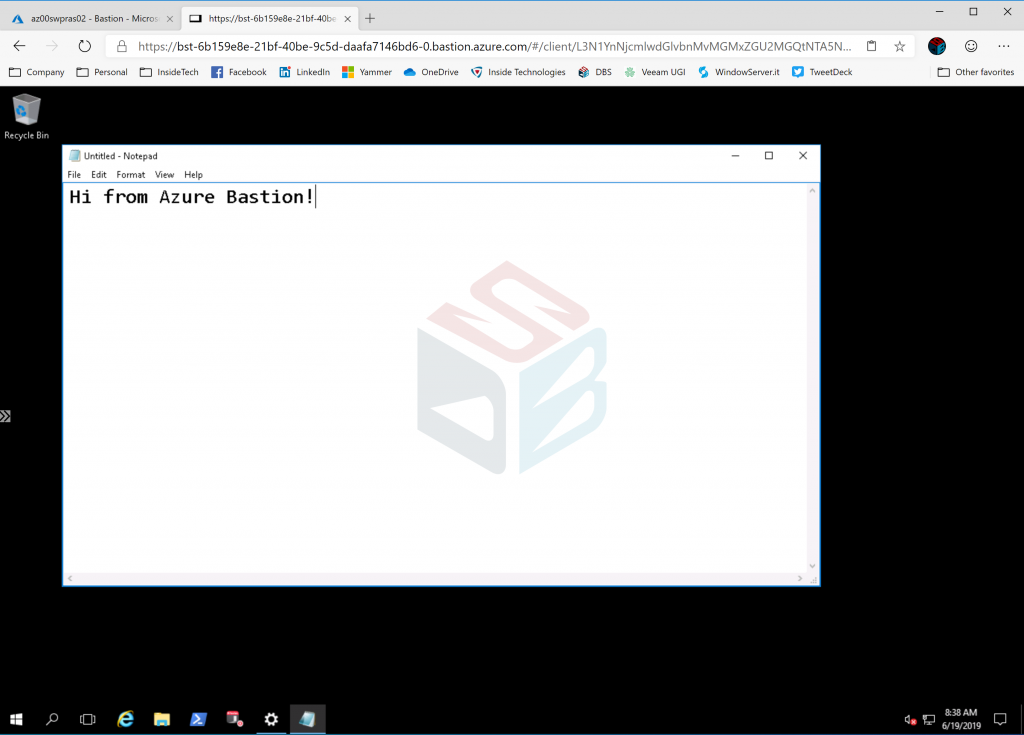
After few seconds the machine will be available from web!
Conclusion
Azure Bastion is absolutely the future of remote connection, because increase the security and allows IT admins to avoid RDP and SSH to manage their server easily from a web browser and this means also make same activities even you are in vacation without your personal laptop.
The product team is working to increase features and support, so right now there are some limitations like the impossibility to copy/paste a file from your local machine to Azure VM.
#DBS