As you know the latest Windows 10 patch, the 2021-03, was not born lucky due a problem with some printer drivers like Kyocera. Microsoft has been tried to fix the issue in two way:
- The update 2021-03 is now marked as available in Windows Update but is not required
- A patch to fix the patch is now available
The good news is that this patch is not available in WSUS but only via Windows Update or Microsoft Update Catalog. I don’t understand the reason why but this means keep away Configuration Manager; by the way this can be fixed with manual import of these updates.
Download Updates
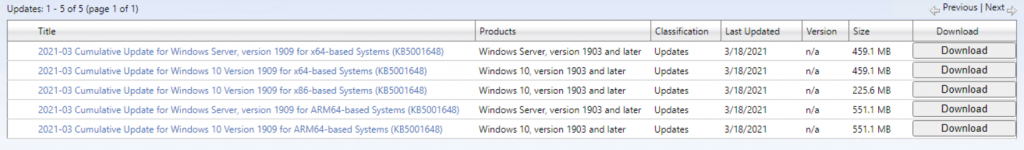
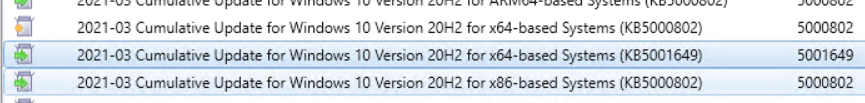
From the MECM server, or where WSUS is installed, open the web site https://www.catalog.update.microsoft.com/ and search all the updates for Windows 10
- KB5001648 for Windows 10 1909
- KB5001649 for Windows 10 2004 and 20H2
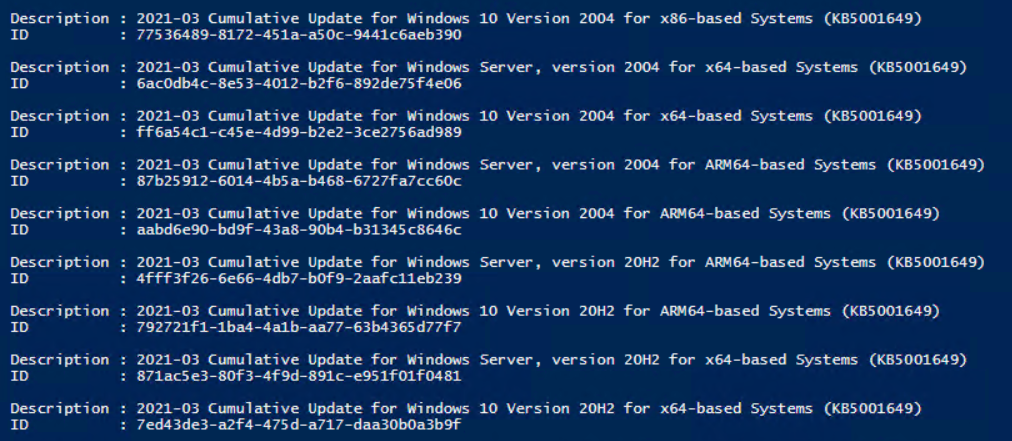
Download the updates into a folder like C:\Temp. Now open a PowerShell ISE and run these cmdlets to find the ID of updates that we want imports:
$kb = Read-Host -Prompt “Enter KB to search?”
$uc = Invoke-WebRequest -UseBasicParsing -Uri “https://www.catalog.update.microsoft.com/Search.aspx?q=$kb“
$uc.Links | where onClick -Like “*goToDetails*” | foreach {($_.outerHTML -replace ‘(<a id=.*?>|</a>)|\s{2,}’,”) + “;” + $_.id -replace ‘_link’,”} | ConvertFrom-Csv -Delimiter “;” -Header “Description”,”ID” | Format-List
Import Updates in WSUS
As you know, MECM/SCCM use WSUS as update engine so we must work on it. Open a PowerShell in Administration Mode and run this cmdlet
$wsus = Get-WsusServer
$wsus = Get-WsusServer -Name <WSUS-FQDN> -PortNumber 8530
$wsus.ImportUpdateFromCatalogSite(‘7ed43de3a2f4-475d-a717-daa30b0a3b9f’, ‘c:\temp\windows10.0-kb5001649-x64_aca549448414a5ad559c742c39e9342468a23eb5.msu’)
Note 1: The ID and the path changes by the update that you need to import.
Note 2: The update for Windows 10 2004 are the same for 20H2 but the ID are different so you need to run the cmdlet twice
Note 3: If your WSUS use SSL, don’t forget to change portnumber to 8531 and add SSL argument
Import Updates in MECM
After few seconds you will be able to run Updates Synchronization in Configuration Manager and after 5 minutes the updates will be available to be downloaded and approved. The download is a “fake” download just because is already available in WSUS.
Troubleshooting
During the import in WSUS can be possible see this message error
To fix these error is necessary remove the legacy protocols with a nice tool called IIS Crypto (or you can follow my article – [Updated] – Disable legacy TLS and SSL in Windows Server).
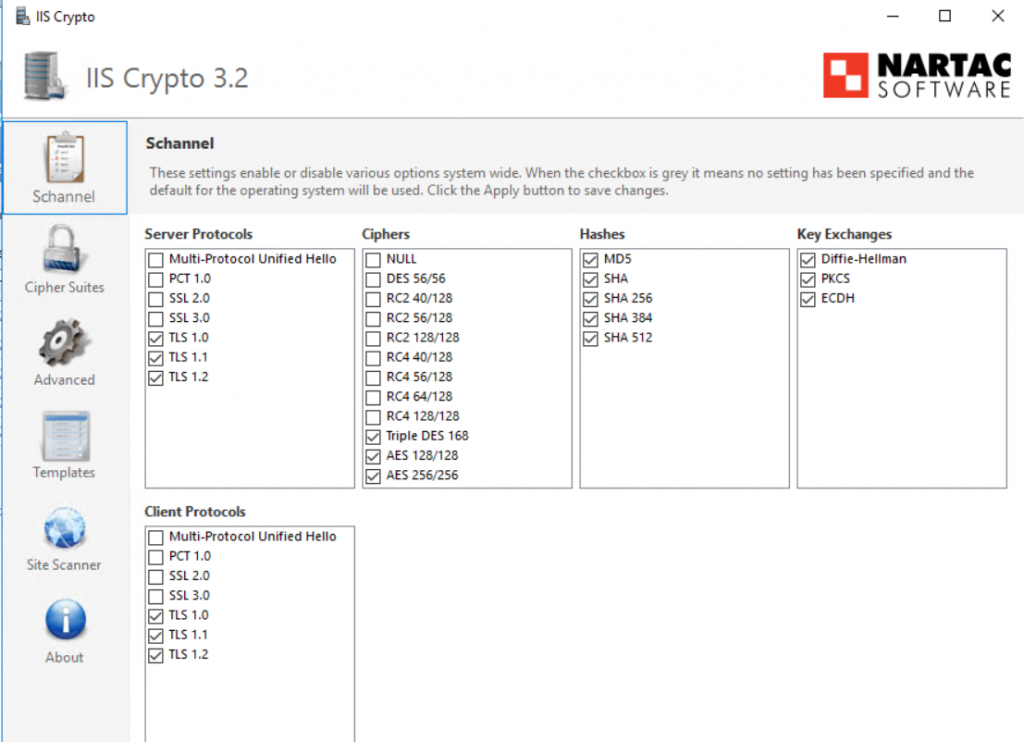
Another point is enable TLS 1.2 for .Net Framework 4 and PowerShell, with these cmdlet:
Set-ItemProperty -Path ‘HKLM:\SOFTWARE\Wow6432Node\Microsoft\.NetFramework\v4.0.30319’ -Name ‘SchUseStrongCrypto’ -Value ‘1’ -Type Dword
Set-ItemProperty -Path ‘HKLM:\SOFTWARE\Microsoft\.NetFramework\v4.0.30319’ -Name ‘SchUseStrongCrypto’ -Value ‘1’ -Type Dword
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12
Don’t forget to reboot the server before run again the import cmdlet.
Conclusion
In few steps you will be able to import updates in MECM even is not available in WSUS.
#DBS